CrowdStrike 2026 Global Threat Report: The definitive threat intelligence report for the AI era Download report
×
![]()
×
![]()
×
![]()
- 01
- 02
- 03
- 04
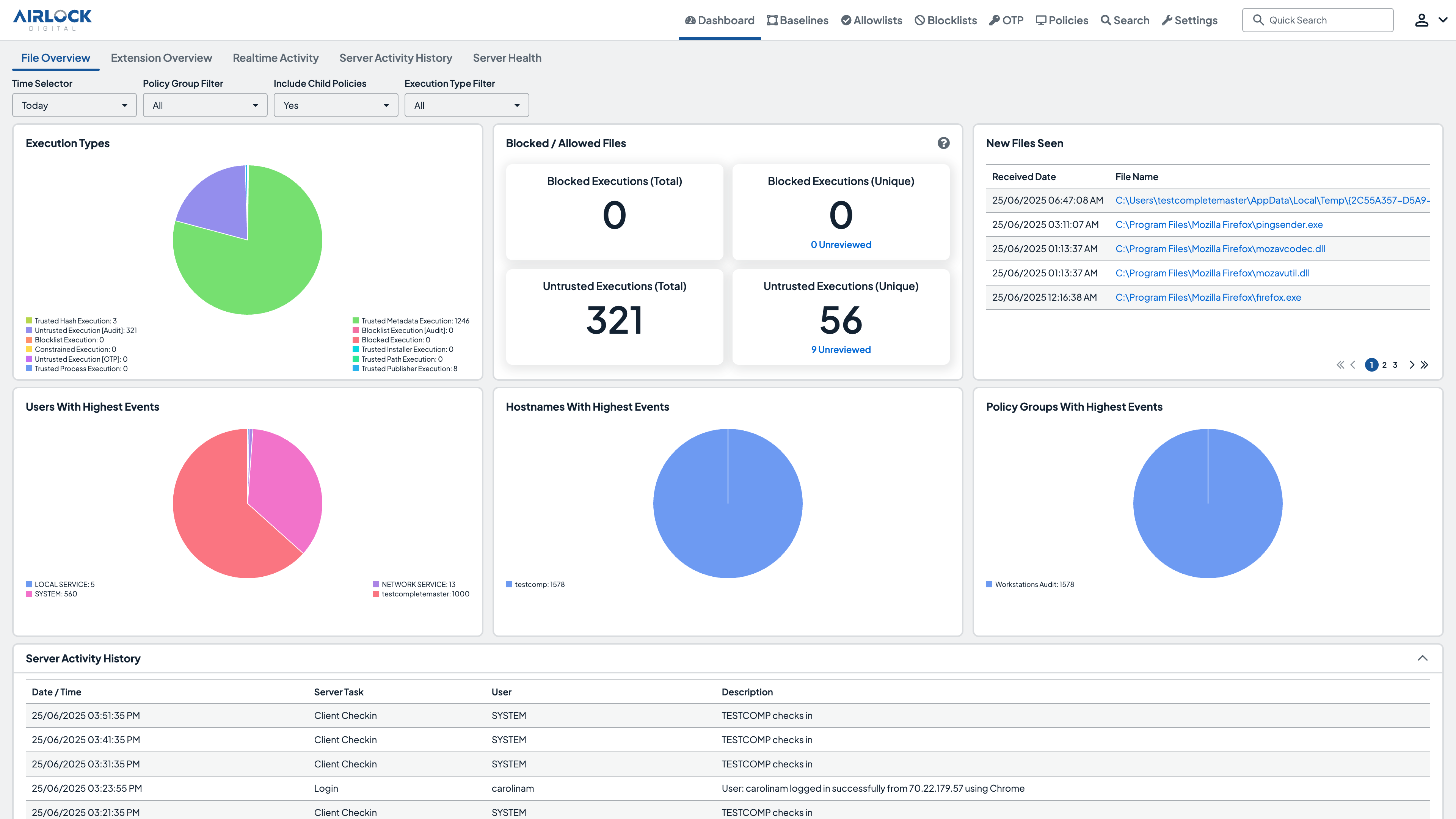
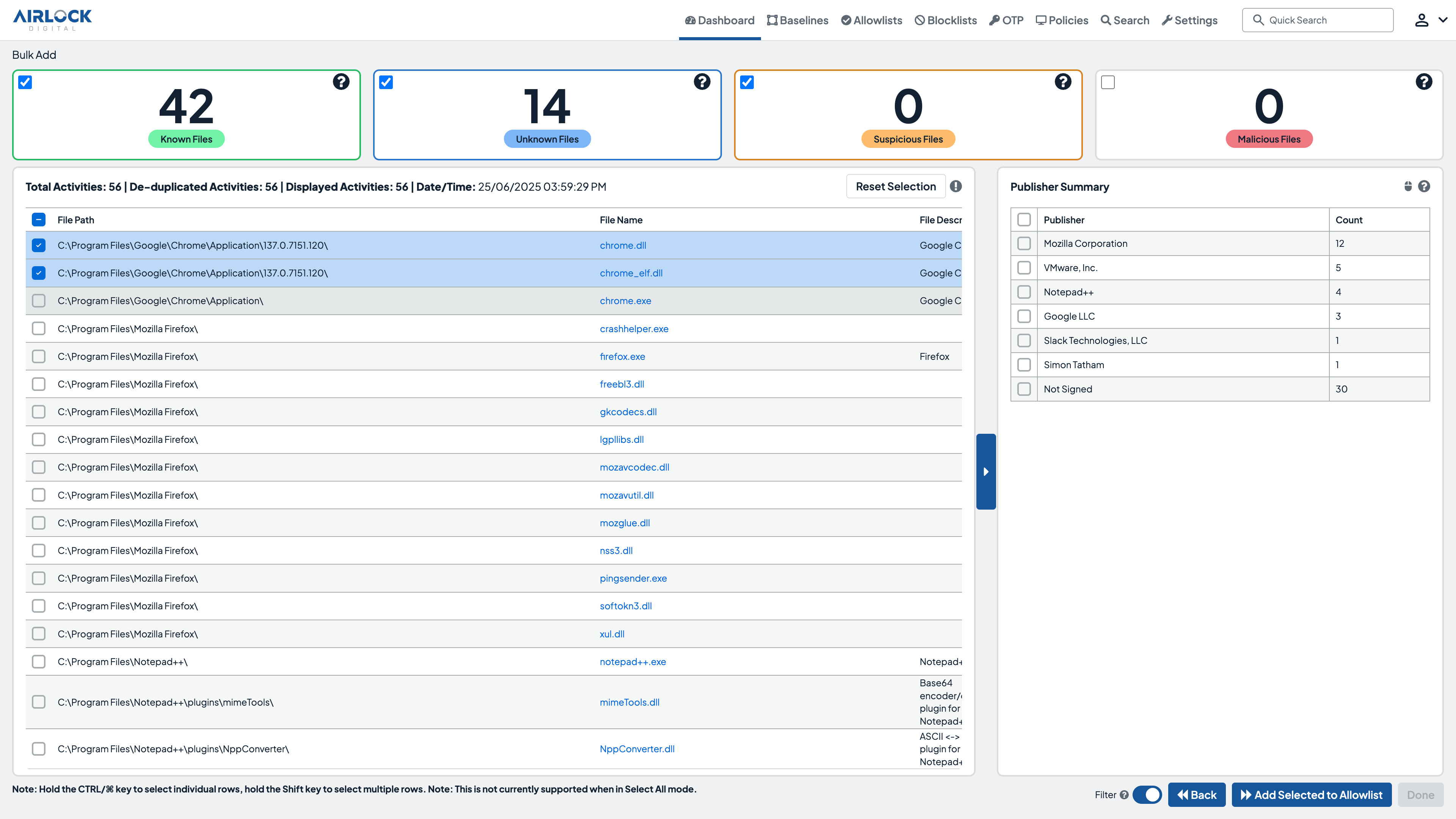
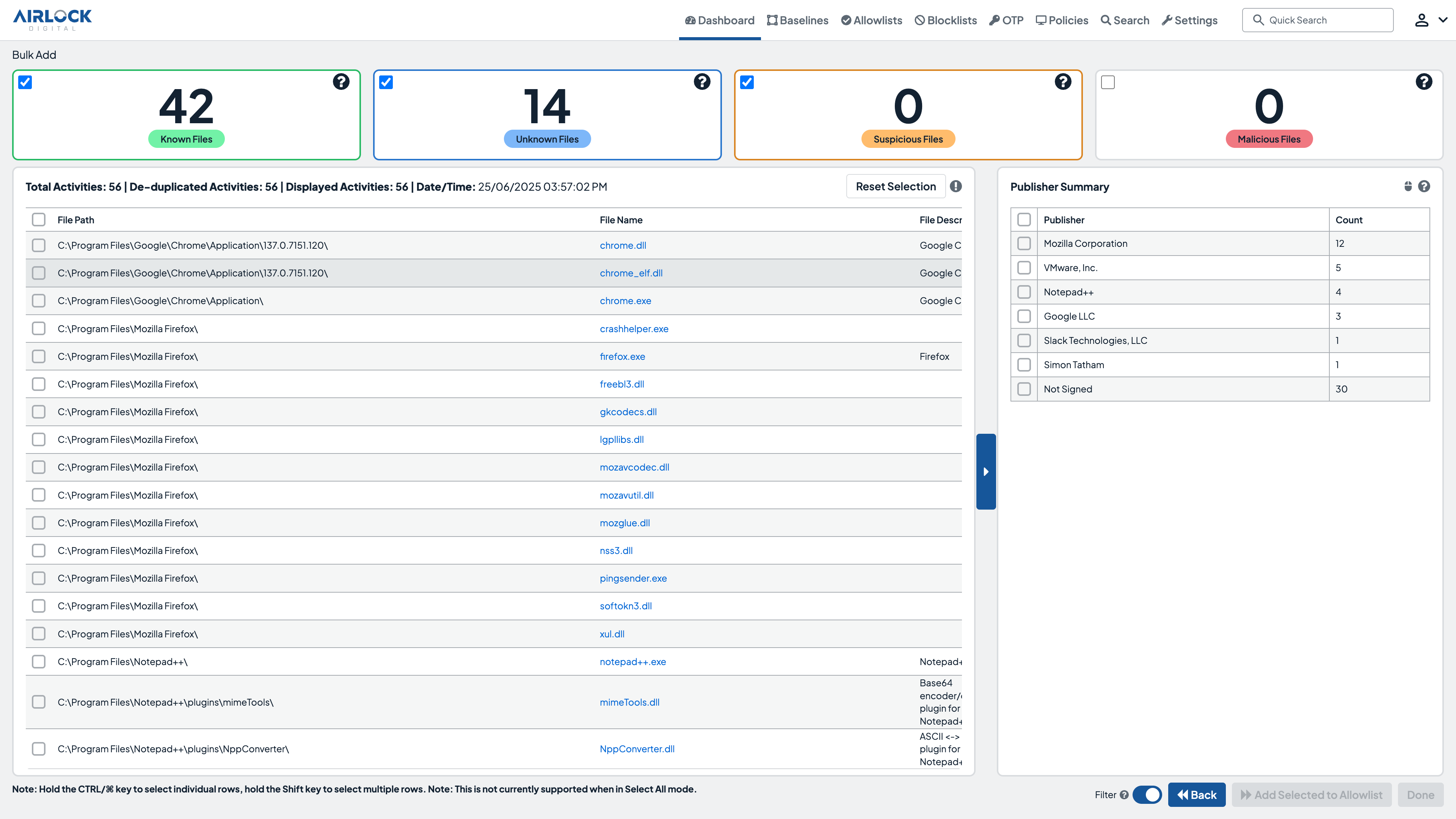
Scalable, easy-to-manage application control & allowlisting
Airlock Digital‘s integration with CrowdStrike Falcon® combines the proactive protection of application allowlisting with the advanced threat detection and response capabilities of CrowdStrike. Together, application control and EDR deliver a robust, defense-in-depth security strategy, preventing malicious applications from executing while enabling rapid response to potential threats.
- Native Integration
Combine Airlock Digital‘s proactive allowlisting with CrowdStrike‘s detection and response to block and respond to threats seamlessly. - Event Correlation
Correlate allowlisting events with CrowdStrike‘s telemetry for a comprehensive view of endpoint activity. - Streamlined Agent Management
Deploy and manage Airlock Digital agents seamlessly via the CrowdStrike Falcon console. - Alert Volume
Reduce the volume of alerts by proactively preventing the execution of all untrusted code.
See customer testimonials and be prepared with the buyer's guide checklist.
Get Started
Deny by Default endpoint security at enterprise-scale
- Native Integration
- Event Correlation
- Streamlined Agent Management
- Alert Volume
Not A CrowdStrike Customer?
Try CrowdStrikeDetails
Built by
Airlock DigitalCategories
Endpoint Security Email Security Web SecurityRequirements
Falcon Insight XDR



