Reach Security Platform
About Reach Security
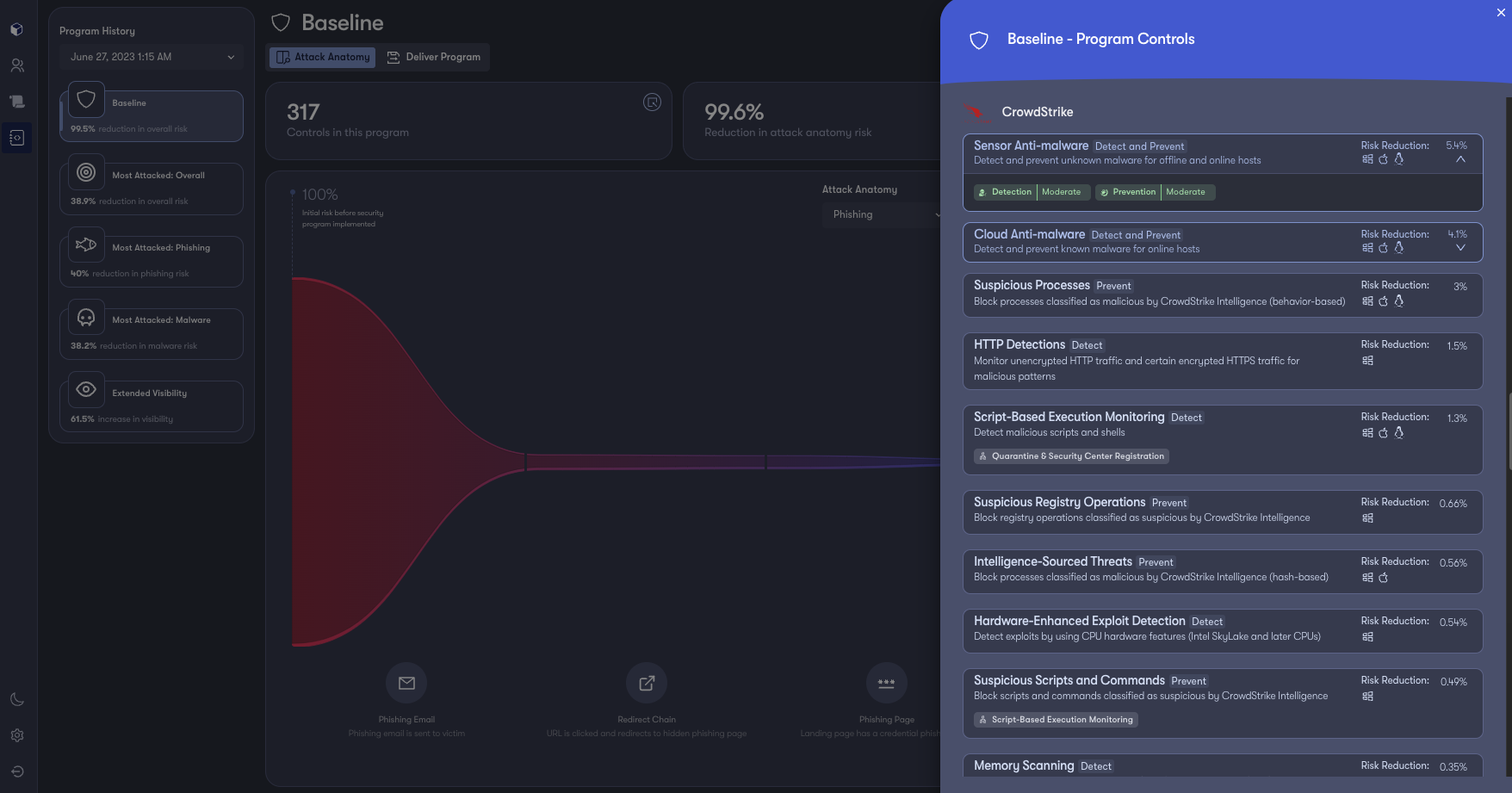
Reach integrates with the broader security estate and pulls threat and event metadata from point products to understand the types of threats targeting your workforce. Reach uses this data to model controls for the CrowdStrike Falcon platform to ensure optimal prevention policies and rules are in place to address risk hotspots. This allows you to deliver the best possible security from your CrowdStrike investments and adapt security policies in real time to address shifts and nuances in risk distribution.
- 01
Tools Rationalization
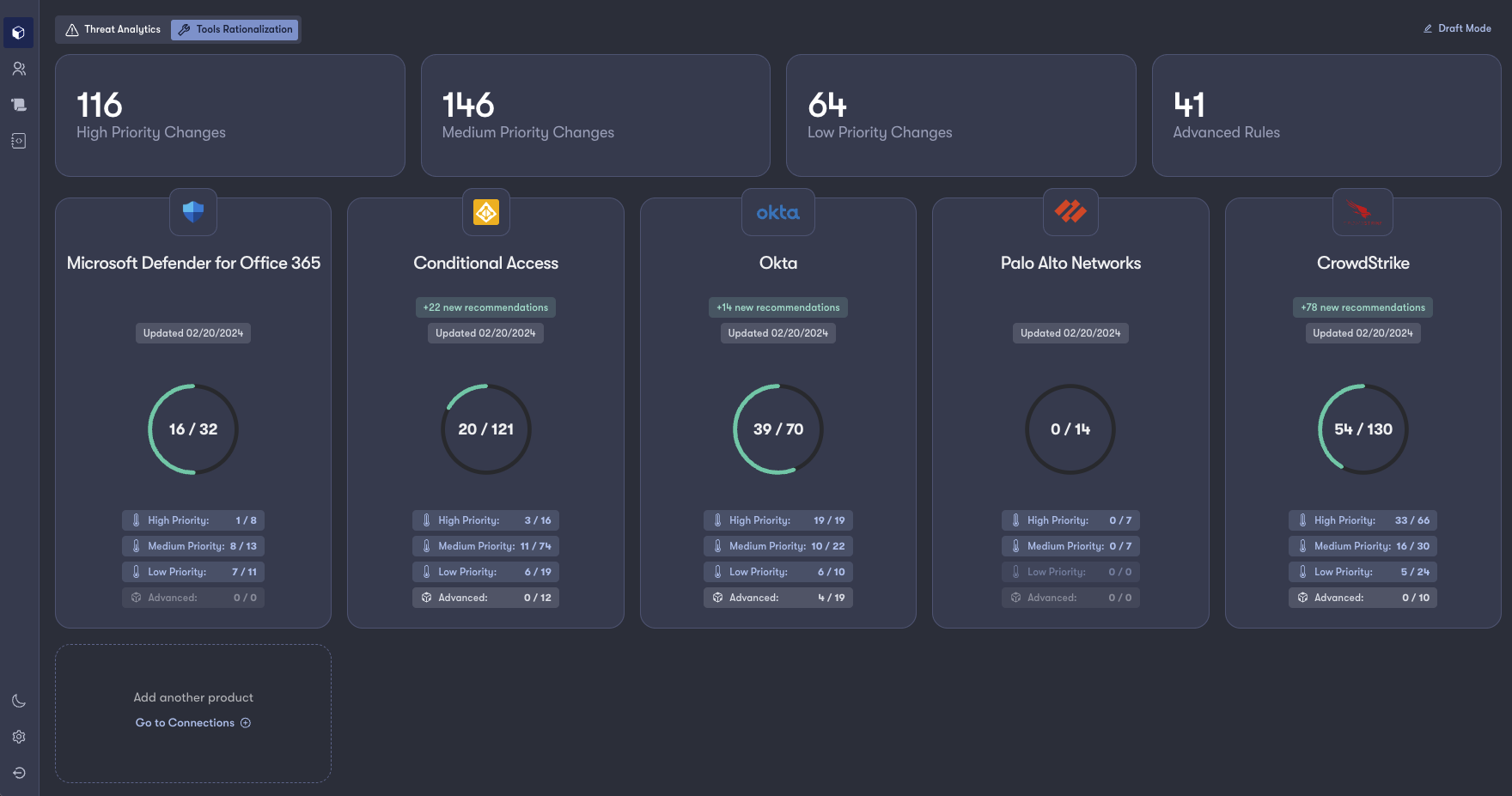
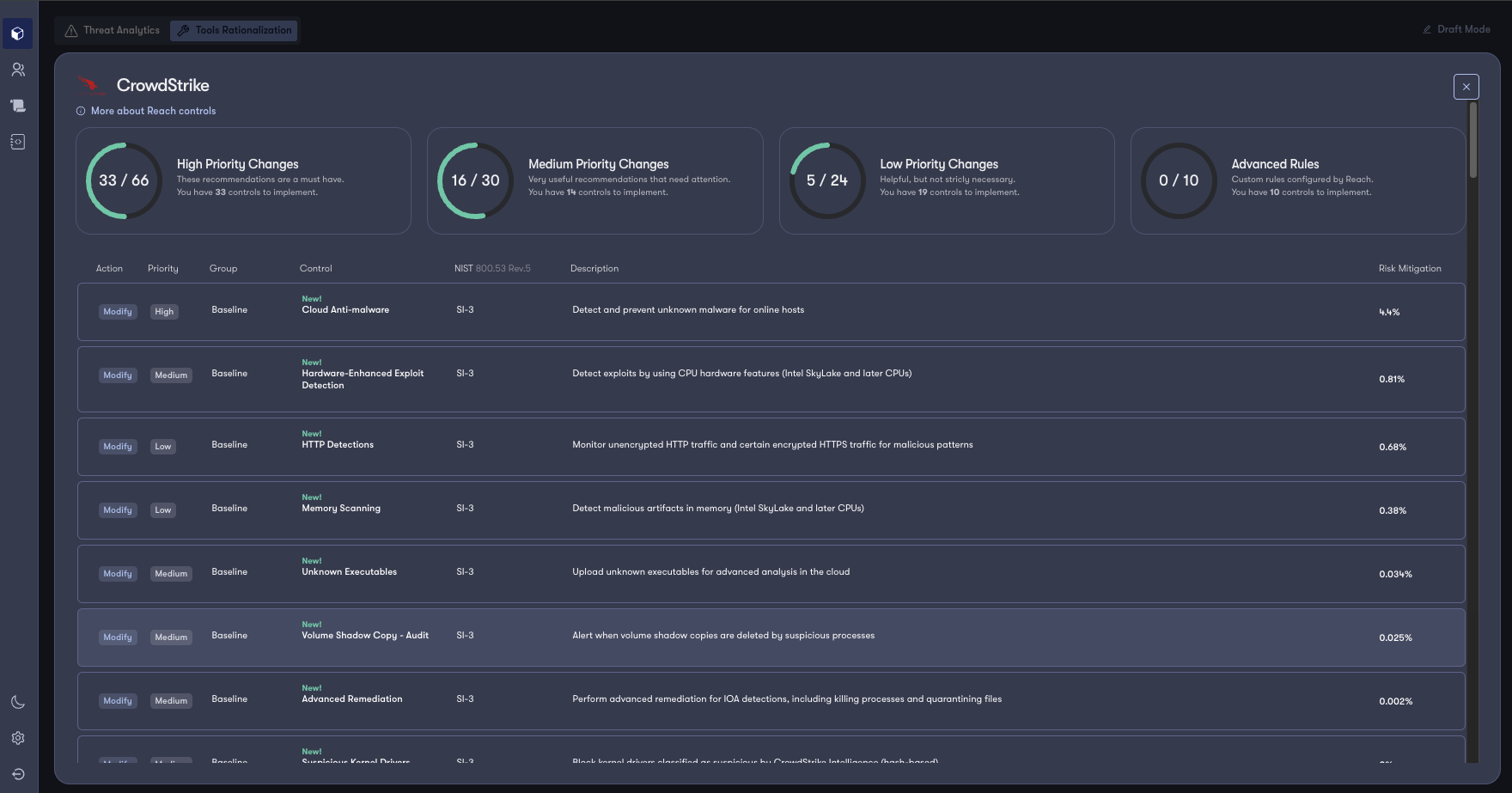
Reach provides immediate visibility into how optimized your products' configurations are relative to threats targeting your users and where risk lives within your workforce.
- 02
Remediate Protection Gaps
Reach serves as an augmentation layer for your defenders by giving them the ability to stage configuration changes directly back to the products to fill protection gaps on an ongoing basis. Reach also provides deployment guides that specify changes details, allowing for streamlined communication amongst teams and change control.
- 03
Continuous Posture Management
As threats, products, and people change over time, Reach adapts to ensure the best possible configurations are in place. This ensures that the capabilities you are licensed for are utilized to the fullest extent possible at all times.