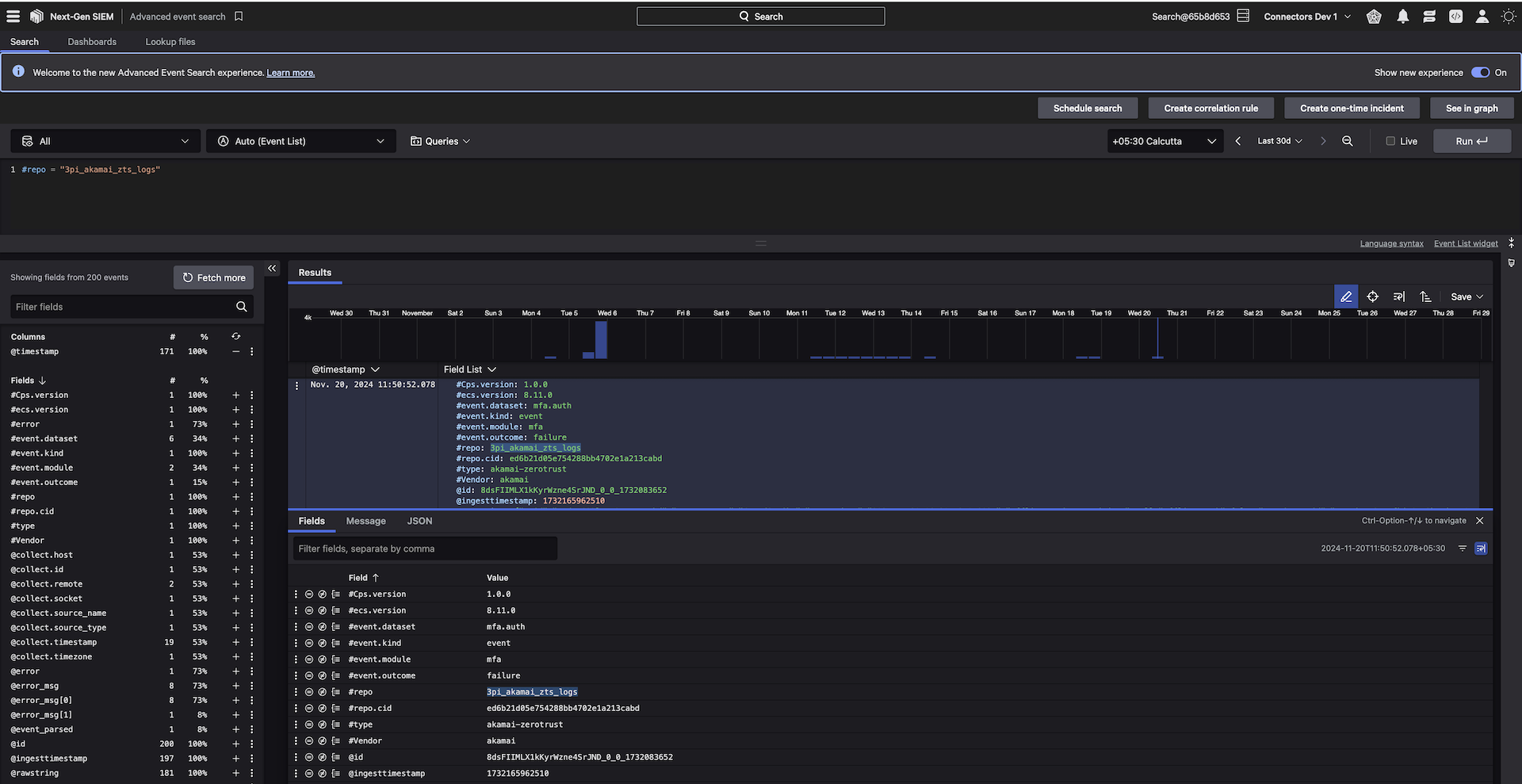
Minimize risk with unified visibility of Akamai Zero Trust Security Logs and Events
Secure your internet access proactively and gain unified visibility by easily ingesting Akamai Zero Trust Security logs including Access Logs, Admin logs, Health logs and Authentication logs into the CrowdStrike Falcon® platform. By centralizing and correlating security events from Akamai Zero Trust Security Services, CrowdStrike, and additional third parties within CrowdStrike Falcon® Next-Gen SIEM, your team gains enhanced vulnerability detection, streamlined incident response, and an optimized security posture to ultimately protect against evolving cyber threats.
- Mitigate configuration risk
Unify visibility of logs and security events by analyzing Akamai Zero Trust Security data with other security telemetry within the Falcon platform - Streamlined investigations and incident response
Accelerate response with detailed timelines of events and actionable forensic data from Akamai Zero Trust Security logs, such as unauthorized access and configuration changes, using built-in search and filtering capabilities from Falcon Next-Gen SIEM - Improve Threat hunting
Store and correlate your security data with other data sources leveraging the Falcon platform as a destination, including real-time detections and blazing-fast search to rapidly shut down threats
Get Started
Easily ingest Akamai Enterprise Application Access (EAA), Enterprise Threat Protector (ETP), Akamai Multi Factor Authenticator (MFA) and Guardicore Segmentation logs into the Falcon platform
- Mitigate configuration risk
- Streamlined investigations and incident response
- Improve Threat hunting
Not A CrowdStrike Customer?
Try CrowdStrikeDocuments





