- 01
- 02
- 03
- 04
- 05
About iboss Zero Trust SSE
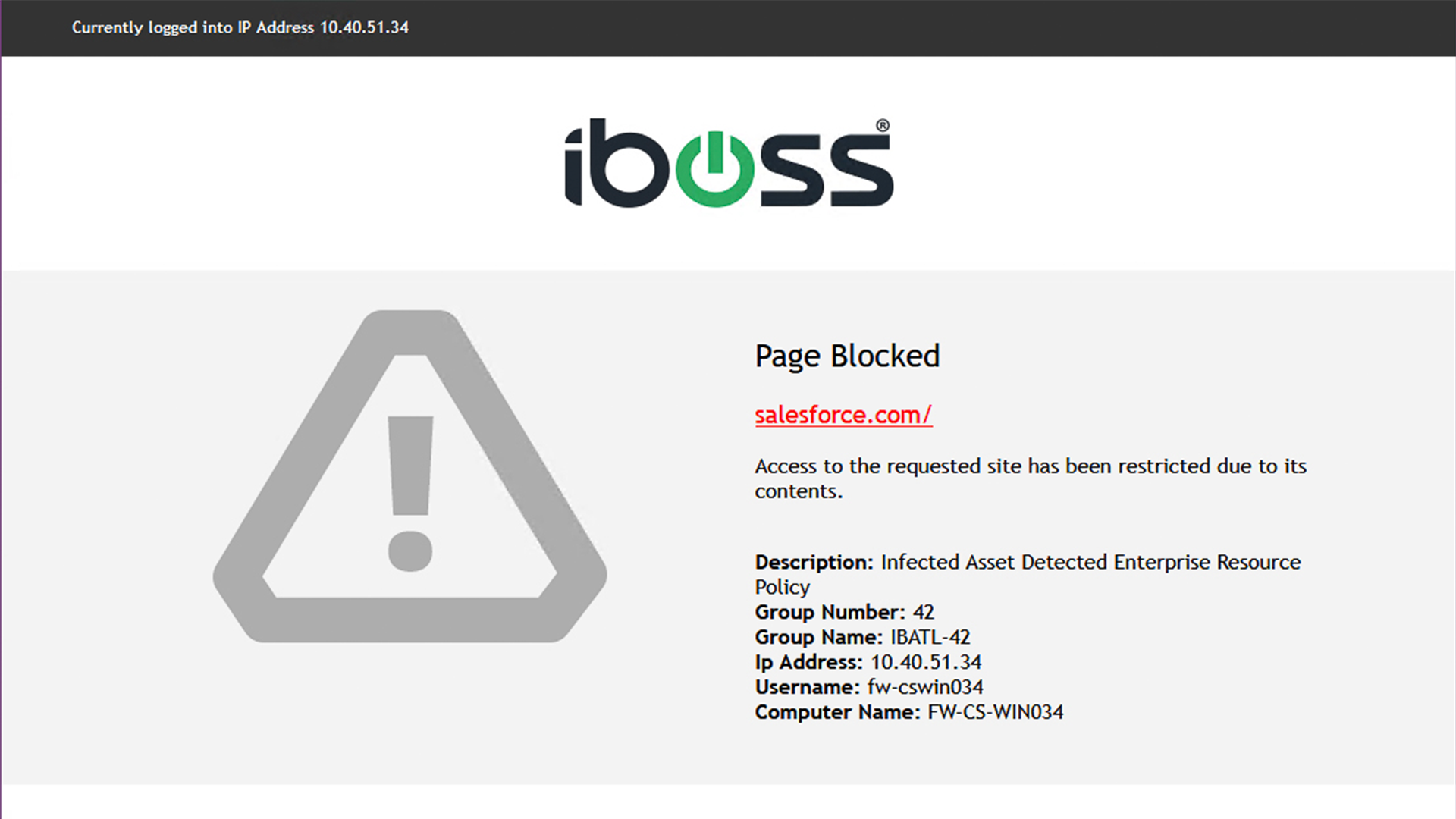
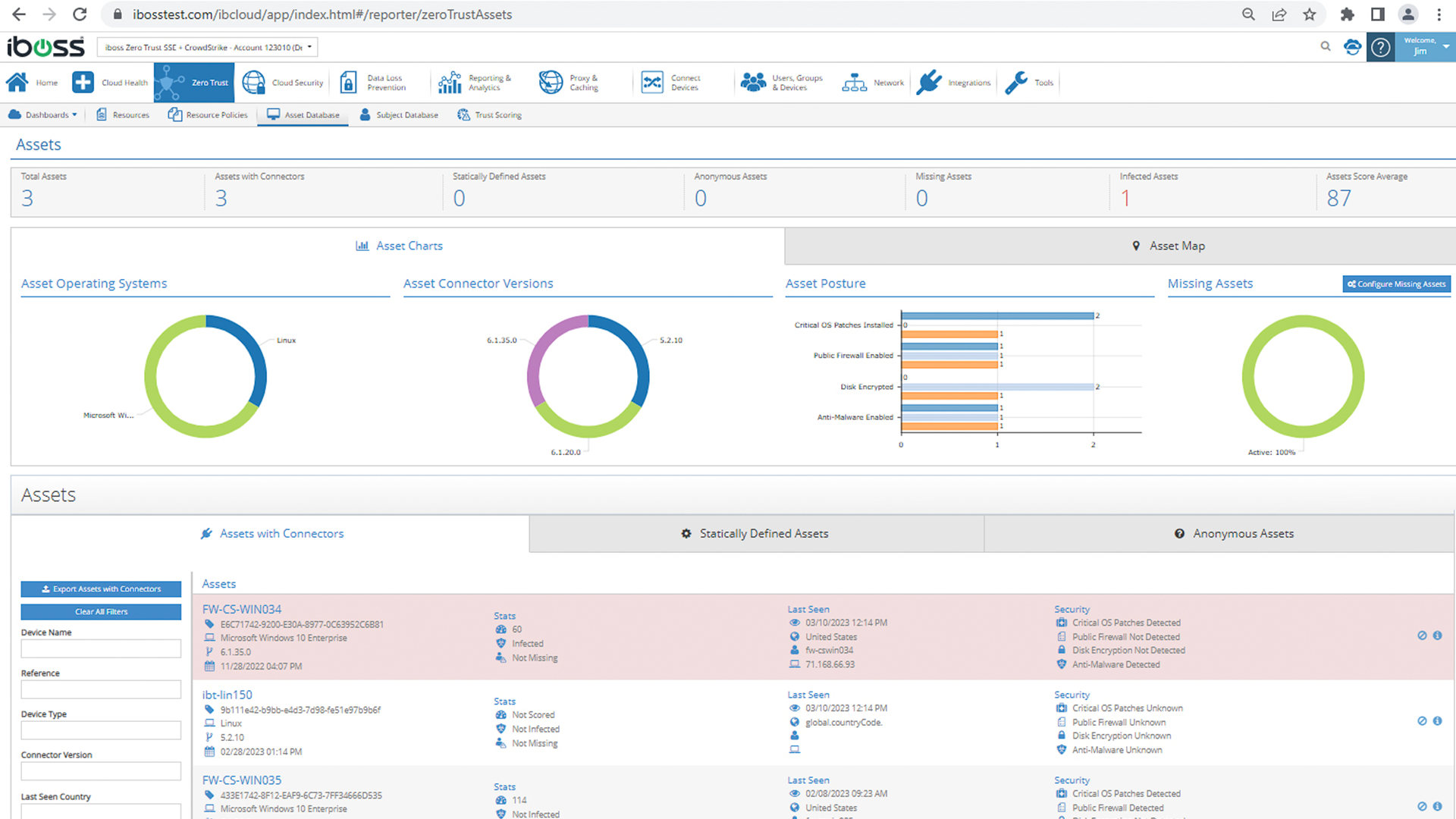
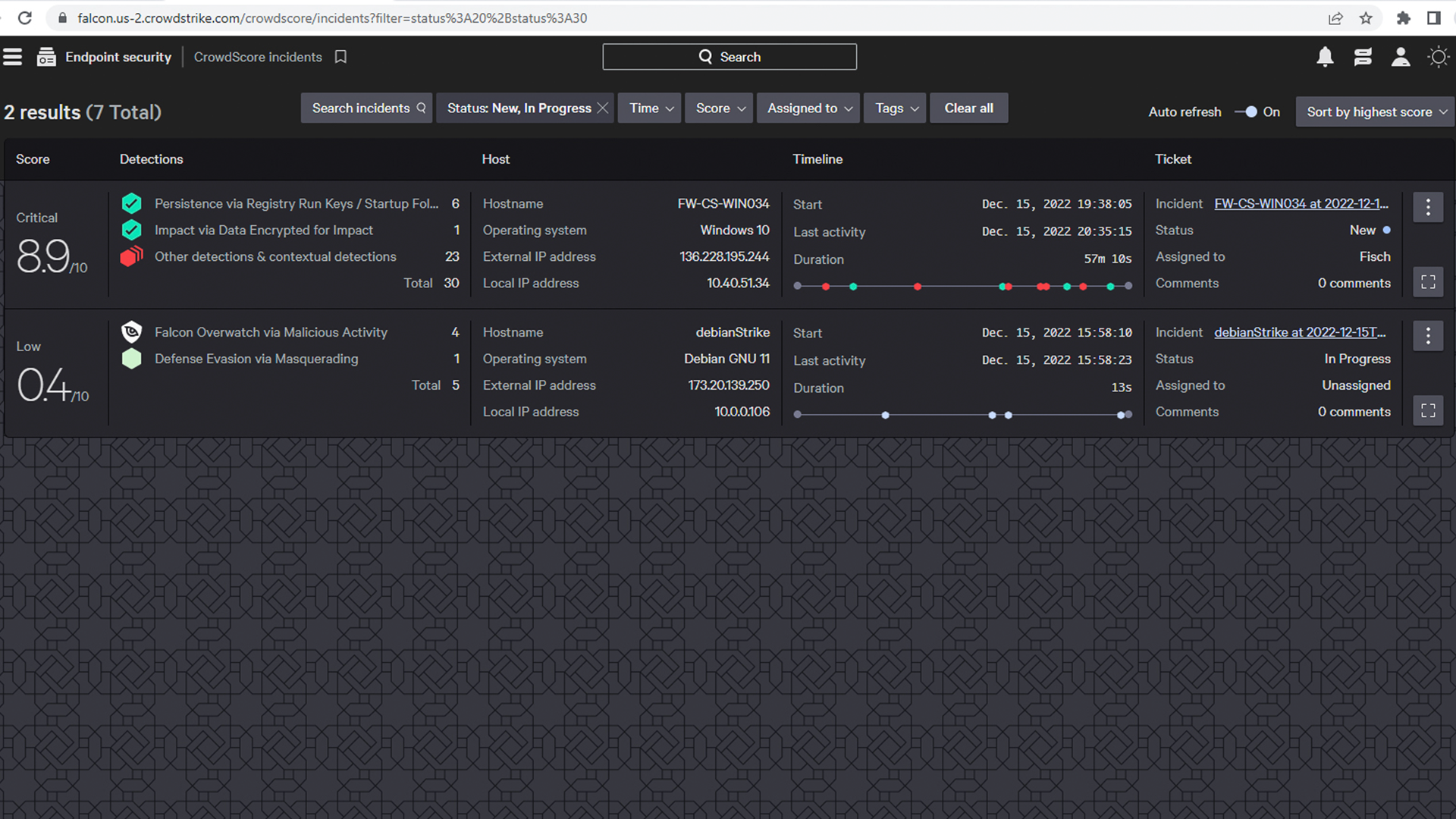
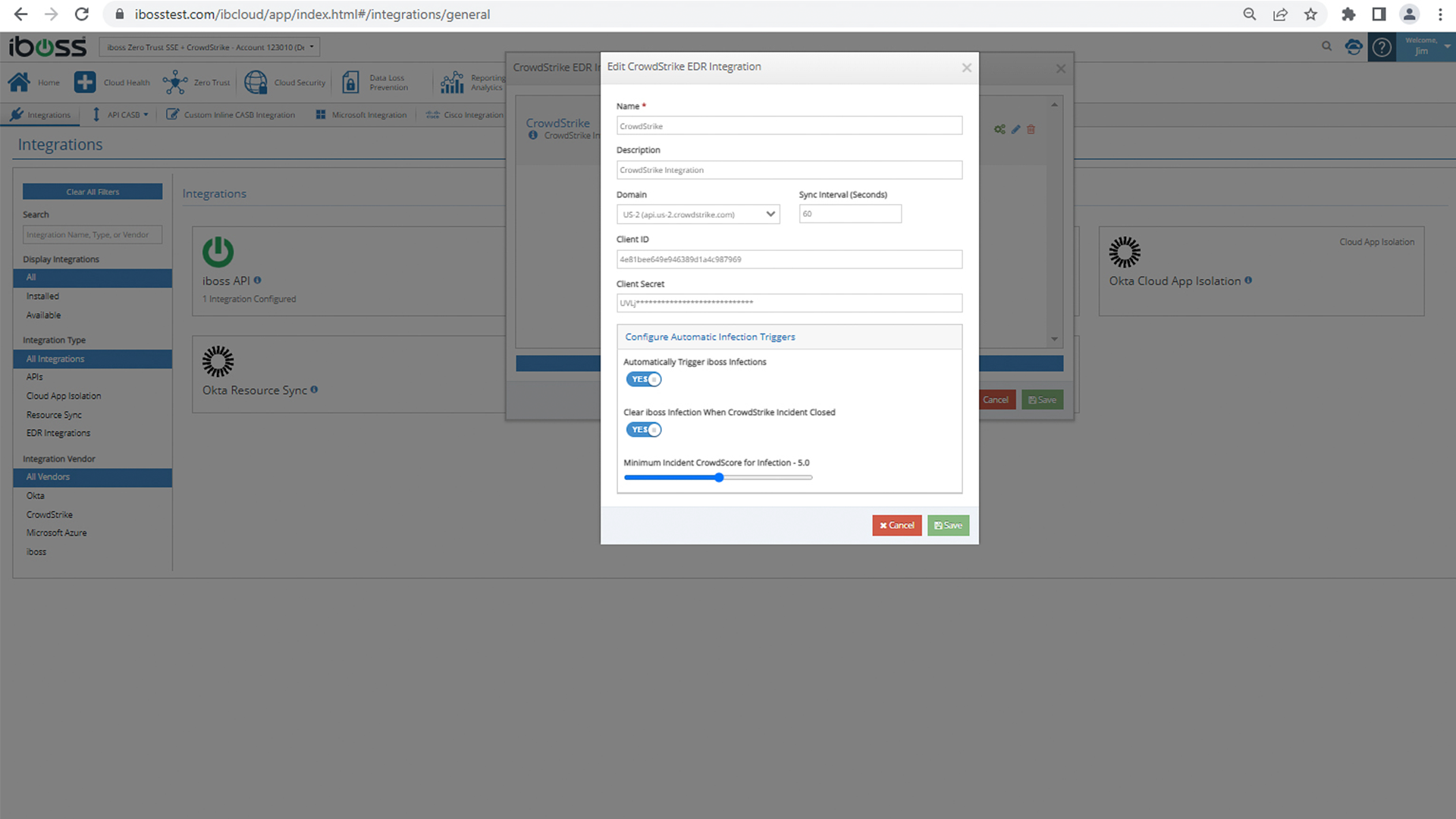
The iboss Zero Trust SSE integrates with the CrowdStrike Falcon® platform to deliver instant and automated actions, including cutting access to sensitive resources when a device becomes infected or identified as high risk. The iboss Zero Trust SSE provides Zero Trust Network Access (ZTNA) and Security Service Edge (SSE) capabilities to control access to enterprise resources while applying CASB, malware defense, compliance policies, DLP, and generating logs for every interaction between users, devices, and sensitive resources. The iboss Zero Trust SSE connects with CrowdStrike to deliver user, asset, and resource protection by exchanging information related to CrowdStrike device and incident risk scores. The integration leverages the CrowdStrike Falcon Zero Trust Assessment (ZTA) risk score and the CrowdStrike CrowdScore®, which indicates device and user risk and incident risk based on severity level. This ensures that access to sensitive applications and data can be automatically terminated by iboss when scores reach critical levels.
- Reduce the time between infection and response
Leveraging the CrowdStrike CrowdScore, the iboss Zero Trust SSE can automatically cut access to resources when a CrowdStrike Falcon incident reaches a critical level. - Minimize the risk of breaches, data loss, and attacks
iboss Zero Trust SSE can take action when the Falcon ZTA score indicates high risk; actions can include automatically cutting off access to sensitive resources or adding a pane of glass in front of resources using Browser Isolation. - Automatically grant or deny access to applications, data, and services
The iboss Zero Trust SSE automatically clears incidents when those incidents are cleared within the Falcon dashboard, restoring access to enterprise-owned resources automatically.
Get Started
Automatically cut, isolate, or adapt access to critical resources based on real-time threats
- Reduce the time between infection and response
- Minimize the risk of breaches, data loss, and attacks
- Automatically grant or deny access to applications, data, and services
Not A CrowdStrike Customer?
Try CrowdStrike



