CrowdStrike 2026 Global Threat Report: The definitive threat intelligence report for the AI era Download report
×
![]()
Accelerate operations and boost threat detection
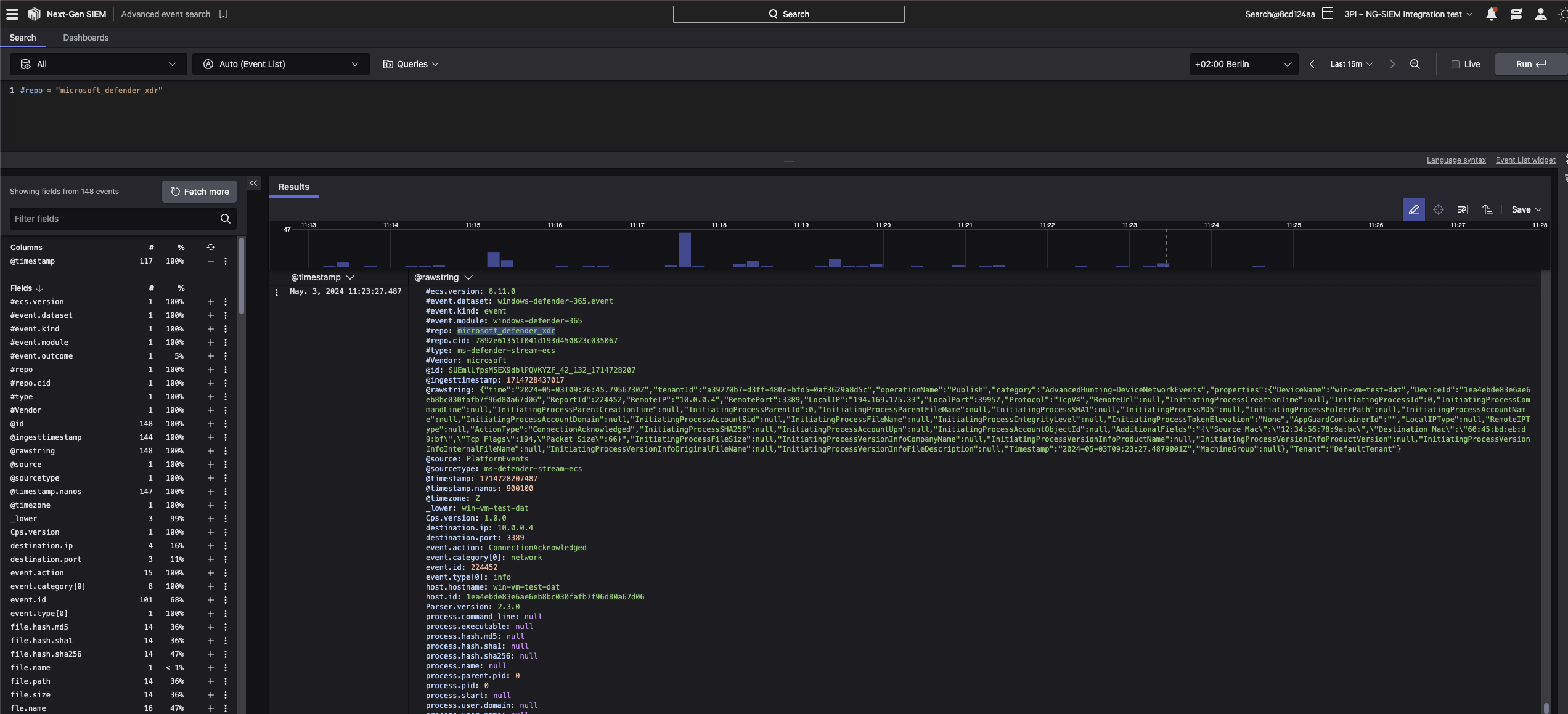
Secure your end-to-end environment and gain unified visibility by easily ingesting Microsoft Defender XDR events into the CrowdStrike Falcon® platform. By centralizing and correlating endpoint, identity, SaaS application, email and collaboration tool event data from Microsoft Defender XDR, CrowdStrike, and additional third parties within CrowdStrike Falcon® Next-Gen SIEM, your team gains enhanced threat detection, streamlined incident response, and an optimized security posture to ultimately protect against evolving cyber threats.
- Enhance threat detection across the environment
Gain a comprehensive view of your end-to-end environment and potential, elusive threats by analyzing Microsoft Defender XDR events and correlating them with other security telemetry within the Falcon platform - Accelerate investigations and incident response
Speed up response with detailed timelines of events and actionable forensic event data from Microsoft Defender XDR, such as unauthorized access and misconfigurations, using built-in search and filtering capabilities from Falcon Next-Gen SIEM - Improve threat hunting
Store long-term and correlate Microsoft data with other data sources for enhanced threat hunting, leveraging real-time detections and blazing-fast search in the Falcon platform to rapidly shut down threats
Get Started
Easily ingest Microsoft Defender XDR events for further analysis, threat detection and investigation
- Enhance threat detection across the environment
- Accelerate investigations and incident response
- Improve threat hunting
Not A CrowdStrike Customer?
Try CrowdStrike


.png)


