- 01
- 02
- 03
Implement Zero Trust security and boost posture
Enhance your security posture by mapping and securing relationships between users, devices, and applications in real-time with Elisity and CrowdStrike. By ingesting rich security telemetry and posture scores from the CrowdStrike Falcon® platform into Elisity‘s IdentityGraph™, you can ensure only authenticated and authorized entities have access to critical resources for effective Zero Trust security. By combining Elisity's identity-based microsegmentation with the highest-fidelity security telemetry from CrowdStrike, you gain a robust, proactive defense against cyber threats, streamlining compliance and bolstering overall network security.
- Asset verification to reduce breach risk
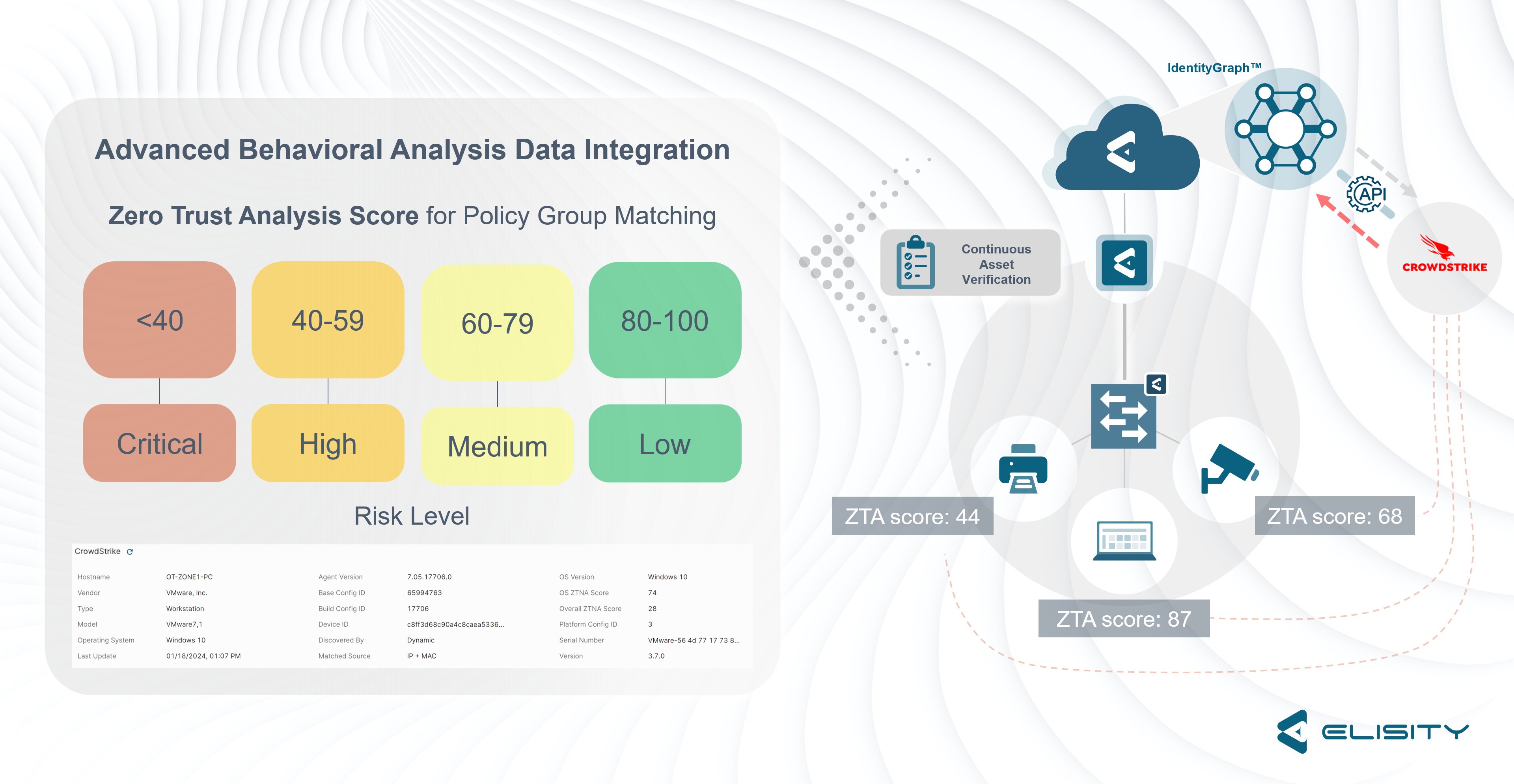
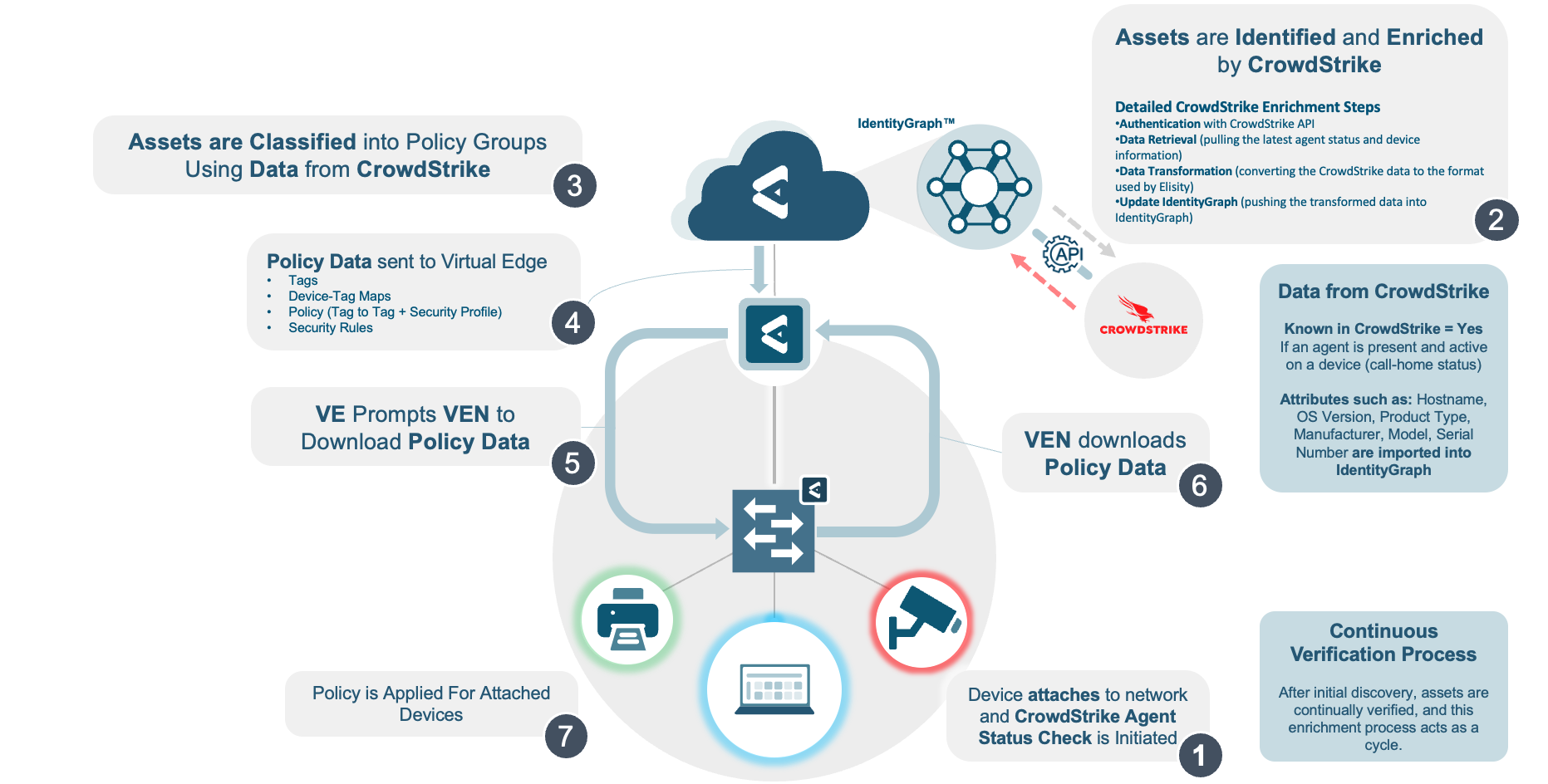
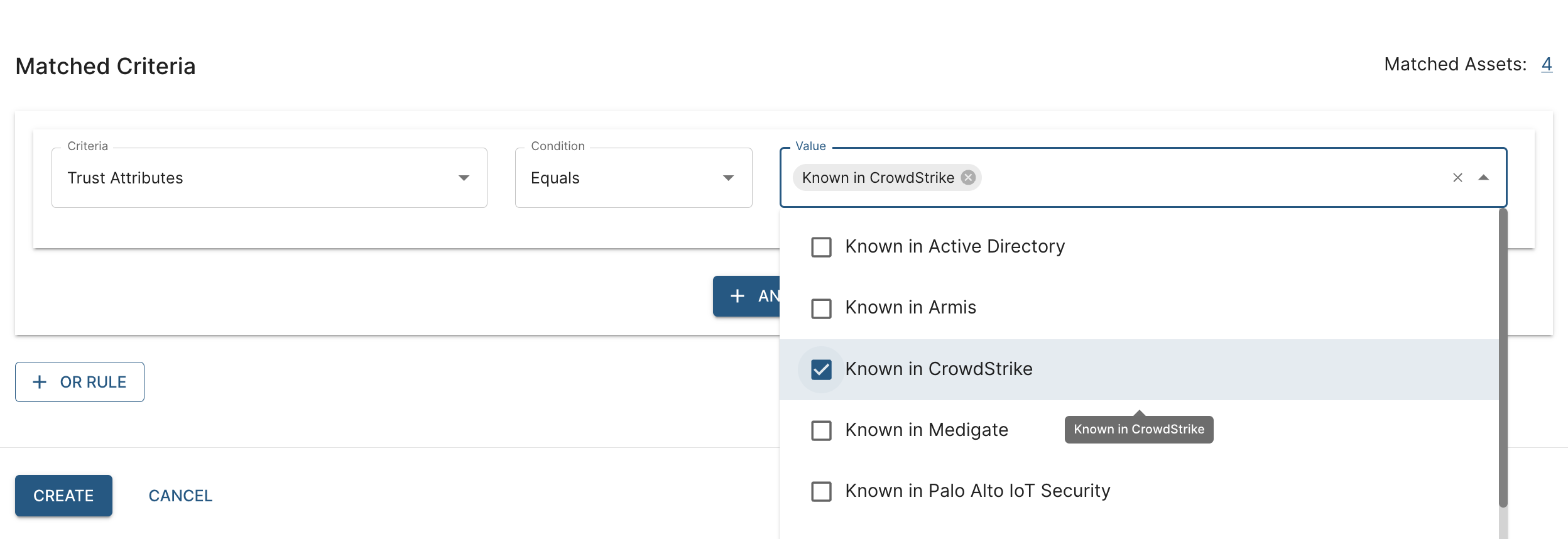
Leverage rich CrowdStrike security and device data within Elisity to verify that only authorized network assets, with a confirmed device security posture, gain access to its environment, preventing unauthorized access and ensuring network policies target the correct assets - Data enrichment for discovered devices
Enrich Elisity's IdentityGraph™ of mapped network interactions with additional device context from CrowdStrike, including identity and security status of devices, to customize network security measures based a device's unique risk profile for informed, granular policy enforcement and access control decisions - Dynamic policies based on trust scores
By using CrowdStrike Falcon® Zero Trust Assessment (ZTA) scores in Elisity‘s access control framework, you can determine an asset's trustworthiness to then dynamically adjust policies as the trust levels of devices evolve for effective Zero Trust security
Get Started
Enhance security posture with context-aware policies for users, devices, and applications
- Asset verification to reduce breach risk
- Data enrichment for discovered devices
- Dynamic policies based on trust scores
Not A CrowdStrike Customer?
Try CrowdStrikeDetails
Built by
ElisityCategories
Network and Infrastructure SecurityRequirements
Falcon Insight XDR




