- 01
- 02
- 03
- 04
- 05
Real-time deterministic threat identification and containment
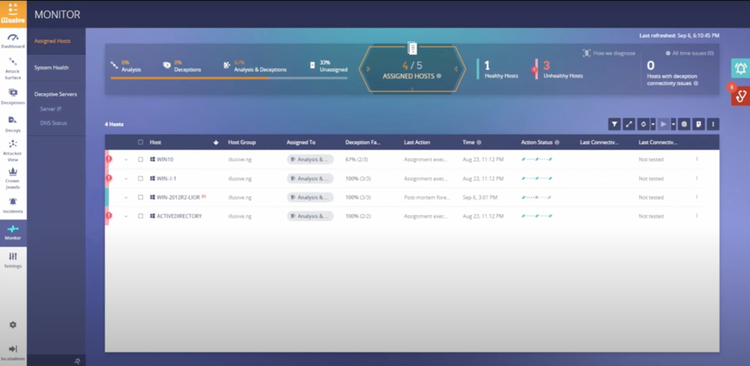
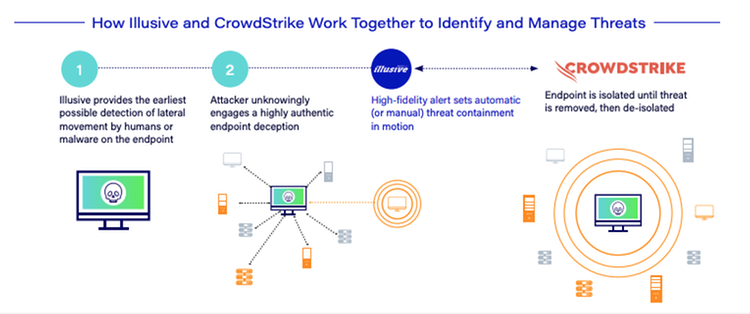
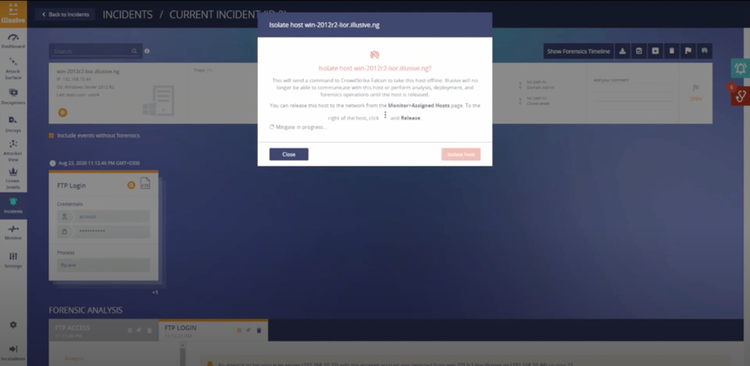
Illusive integrates with the CrowdStrike Falcon® platform to deliver real-time threat detection and instant isolation of compromised endpoints at the earliest point of attack. Illusive deception-powered Active Defense provides high-fidelity notifications that CrowdStrike customers can consume to automatically or manually isolate suspicious endpoints in milliseconds. Upon receipt of an Illusive alert from the endpoint, users can isolate compromised hosts in real-time leveraging the Falcon platform. It‘s a fast way to stop an endpoint-based threat once it is reported by Illusive. With Illusive and CrowdStrike, you can identify threats early in their life cycle, reduce response time, and gain the visibility needed to mitigate attacks before they get near critical assets.
- Complement threat detection with Illusive's deterministic high-fidelity alerts based on direct attacker interaction
This integration pairs Illusive's deterministic alerting with the Falcon endpoint detection and response (EDR) solution to respond and contain a compromised host until the threat is removed. Illusive‘s deterministic deception-based threat detection is not dependent on the existence of attack tools, malware or exploits, but on actual human engagement. - Automatic or manual isolation of comprised hosts before attackers can move laterally toward critical assets
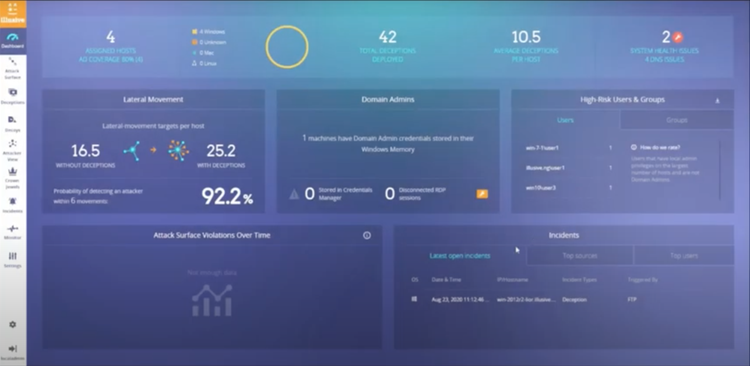
When pairing Illusive‘s deterministic, high-fidelity alerting with CrowdStrike‘s instant ability to respond and contain a compromised host until the threat is removed, organizations—especially those that lack extensive security resources—gain tactical advantage over adversaries armed with context-rich forensics that saves valuable hours of manual investigation efforts. - Collect additional, actionable forensic data about attackers and endpoints
Illusive can collect forensics on any machine and return precise intelligence in seconds that usually requires hours of manual activity. In addition, all forensic data is compiled in a chronological timeline per incident and presents it in a sortable, human-readable format that accelerates incident analysis.
Get Started
Deterministic threat identification and containment
- Complement threat detection with Illusive's deterministic high-fidelity alerts based on direct attacker interaction
- Automatic or manual isolation of comprised hosts before attackers can move laterally toward critical assets
- Collect additional, actionable forensic data about attackers and endpoints
Not A CrowdStrike Customer?
Try CrowdStrikeSupport





