CrowdStrike 2026 Global Threat Report: The definitive threat intelligence report for the AI era Download report
×
![]()
×
![]()
×
![]()
×
![]()
- 01
- 02
- 03
- 04
- 05
Providing 360-degree threat containment and remediation
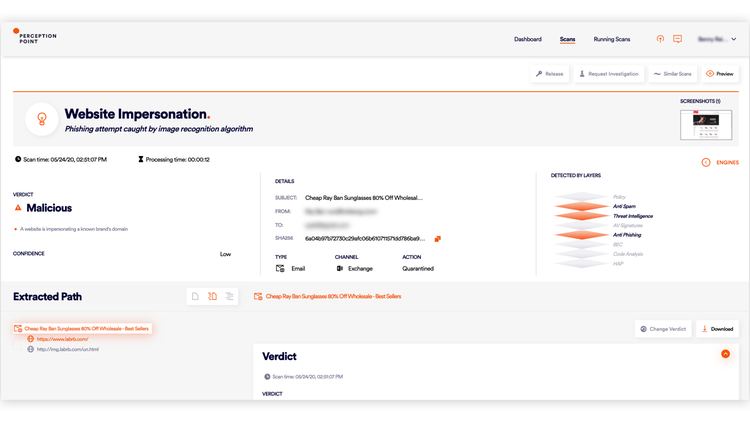
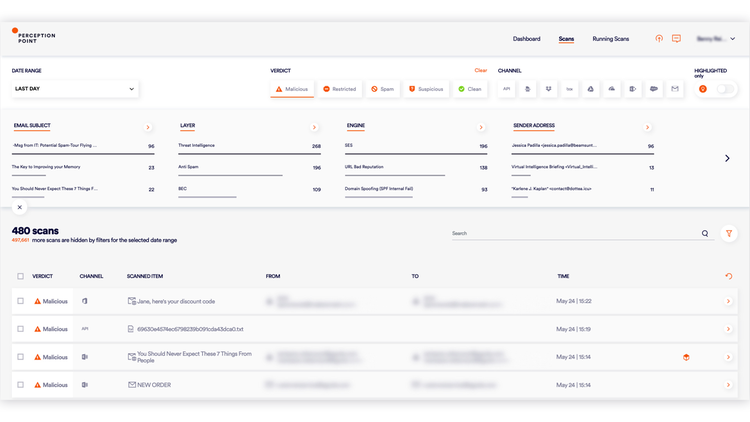
Perception Point‘s X-Ray seamlessly plugs into CrowdStrike Falcon® to contain and remediate malicious incidents that successfully breach the enterprise and are subsequently detected on the endpoint. Instant and automated, X-Ray scans all channels (email, CRM, cloud storage and more) to identify where else the content was sent and prevent further transmission. Lightning-fast, unlimited in scale, and covering the range of attack techniques, the X-Ray provides a complete channel audit within minutes, while actively remediating and containing the incident.
- Minimize containment time
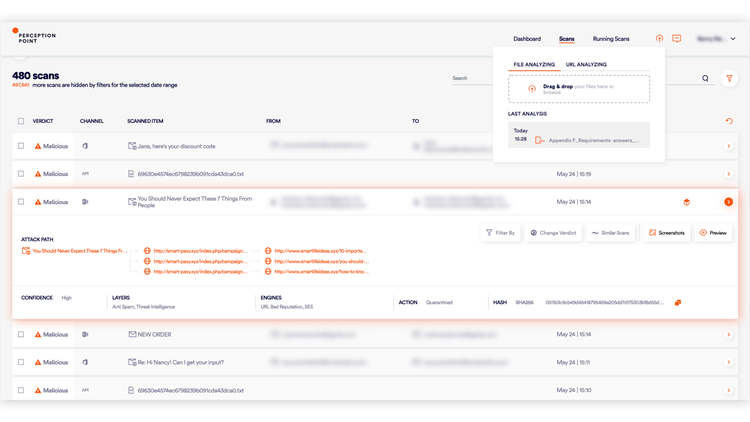
Automated transmission from CrowdStrike Falcon detections to X-Ray enables rapid scan of all channels, dramatically reducing pressure on the SOC team and shortening containment time. - Gain full visibility
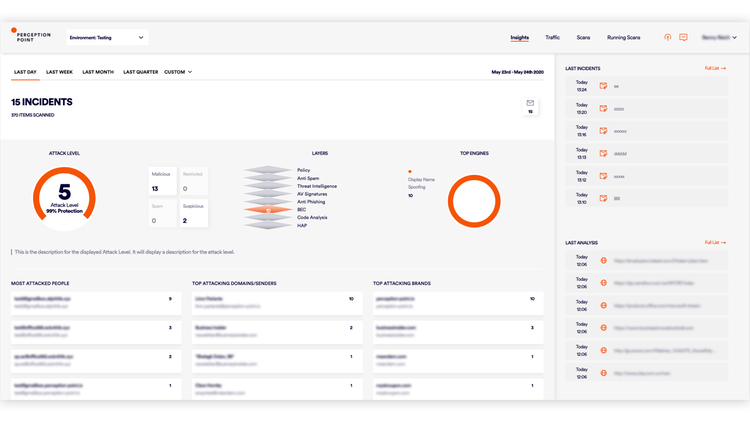
X-Ray maps all affected users through an analysis of cloud content exchanges across the organization to provide full visibility on where else the attack may have spread. - Prevent reinfection
Based on hashes from CrowdStrike Falcon, X-Ray modifies the verdict to "malicious" to prevent reinfection across email and collaboration channels.
Get Started
Preventing any malicious content identified in the endpoint from spreading across the organization
- Minimize containment time
- Gain full visibility
- Prevent reinfection
Not A CrowdStrike Customer?
Try CrowdStrikeDetails
Built by
Perception PointCategories
Cloud Security Email Security Web SecurityRequirements
Falcon Insight XDRSupport




