CrowdStrike 2026 Global Threat Report: The definitive threat intelligence report for the AI era Download report
×
![]()
×
![]()
- 01
- 02
- 03
Discover and remediate compromised email accounts and endpoints
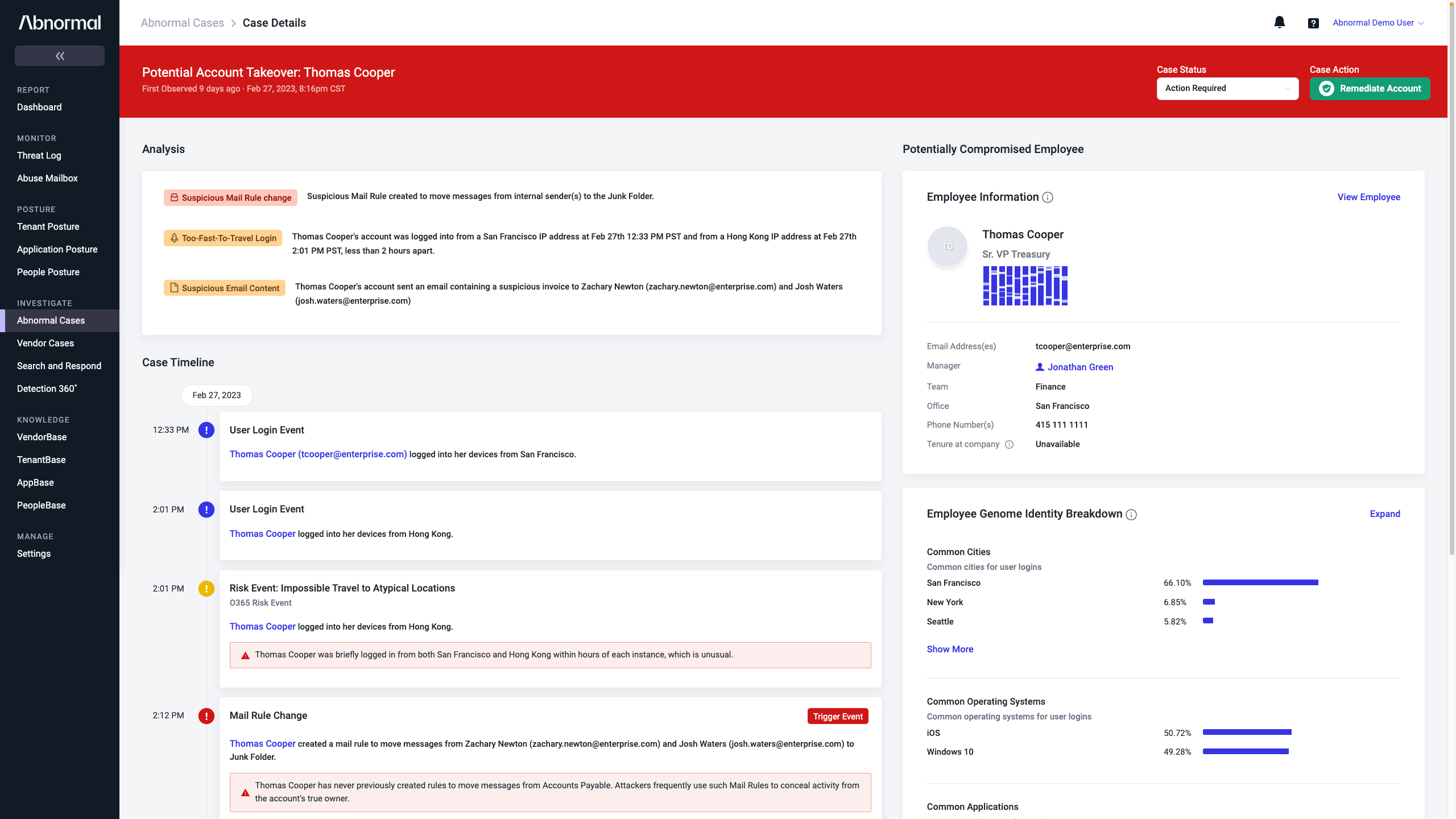
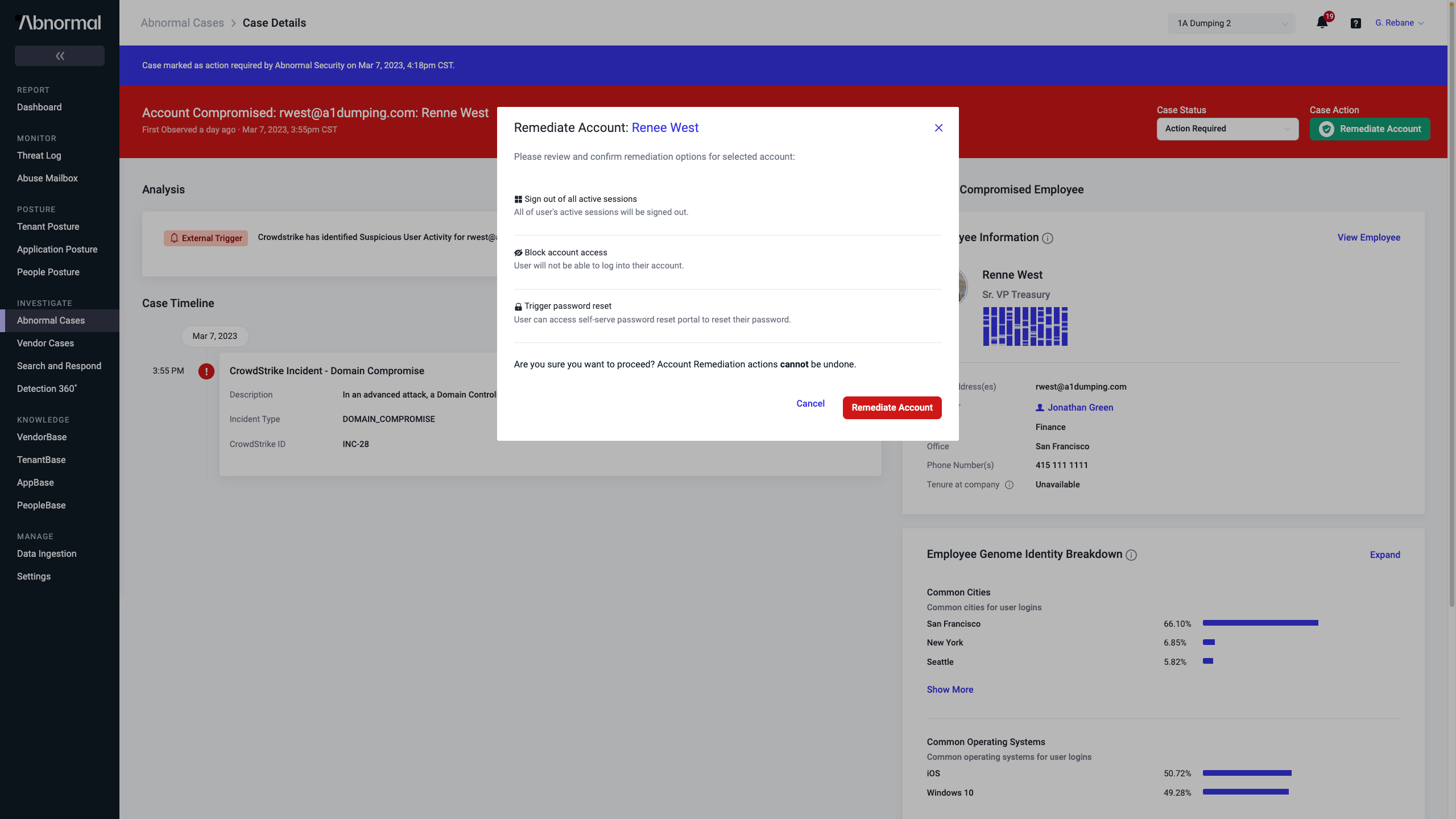
With CrowdStrike and Abnormal Security working together, security analysts can holistically determine whether an identity is behaving normally through continuous behavior analysis from email content, activity, and endpoint monitoring, breaking down siloed views. If a compromise is detected, even if the initial compromise did not occur through email, analysts can act quickly to remediate the connected email account, stopping attacks in progress and mitigating the risk of spread through lateral phishing.
- Detect email account takeovers
When Abnormal detects an active account takeover within a Microsoft 365 account, CrowdStrike will automatically add that user to a Watched Users list within the CrowdStrike Falcon® Identity Threat Protection module - Investigate CrowdStrike identity detections
The Abnormal platform can ingest identity detections from CrowdStrike that indicate, for example, if a host‘s endpoint device has been compromised. Based on this signal, the Abnormal platform automatically opens an account takeover case and shows details of the signal received from CrowdStrike - Orchestrate responses
Analysts can take automated response actions, such as logging the user out, terminating the user session, forcing re-authentication, and more either manually or by leveraging pre-built playbooks
Get Started
Stop the full spectrum of email attacks with advanced behavioral data science
- Detect email account takeovers
- Investigate CrowdStrike identity detections
- Orchestrate responses
Not A CrowdStrike Customer?
Try CrowdStrikeDetails
Built by
Abnormal SecurityCategories
Email Security Cloud SecurityRequirements
Falcon Identity Threat Protection



