- 01
- 02
- 03
- 04
- 05
Defense in depth with cloud-scale cybersecurity strategies
CrowdStrike® and Google Cloud together deliver defense-in-depth security strategies where joint customers can achieve workload protection and visibility at scale and meet compliance requirements across hybrid environments. These integrations between the two cloud-scale platforms leverage powerful APIs and share enriched telemetry to help deliver powerful security benefits. Gain insight into the scope and nature of organizations' Google Cloud resources, so you can secure all virtual machines, uncover and mitigate risks, and reduce the attack surface across your cloud footprint. You can also achieve comprehensive visibility into GCP workload events and compute instance metadata to ensure that nothing goes unseen in your cloud environments. Prioritize violations and investigate alerts, anomalies and threats with improved contextual insight, and proactively stop cyber-attacks.
- Google Chronicle
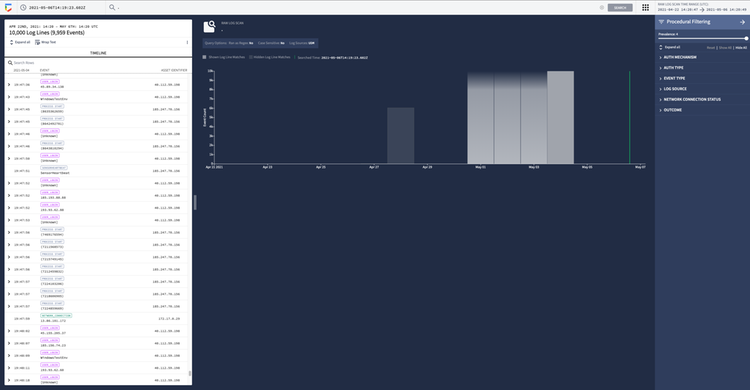
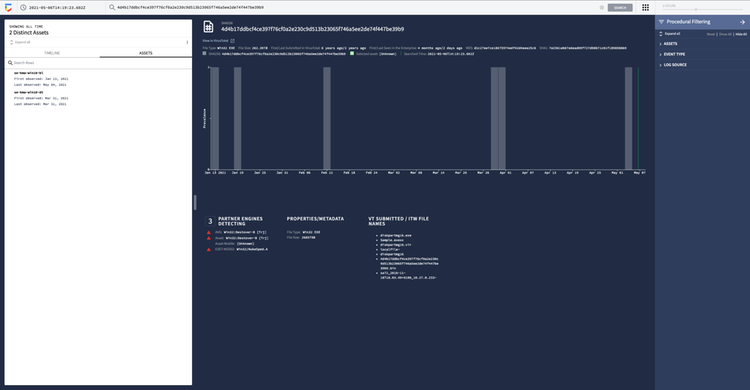
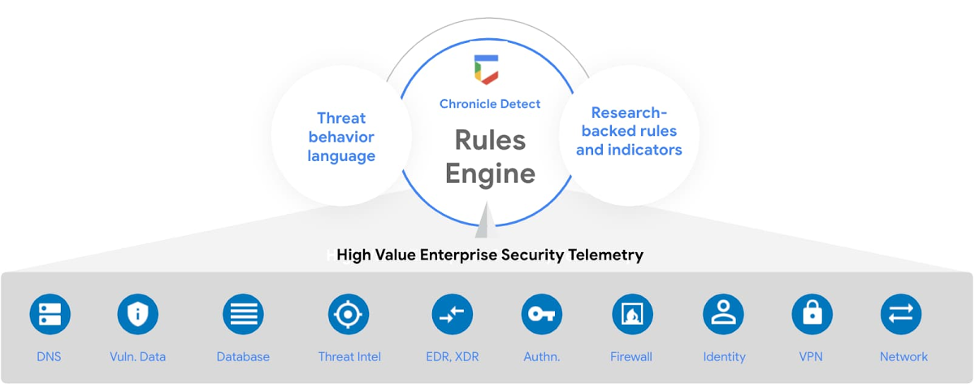
Cost effectively store and analyze all security data in one place to investigate and detect threats at Google speed and scale. Hunt for threats across live and historical endpoint and workload security telemetry at unprecedented speed, with shared indicators of compromise (IOCs) across Chronicle and the CrowdStrike Falcon® platform, providing proactive security. Search across petabytes of data and correlate enriched datasets from the Falcon platform to thoroughly investigate sustained, long-term attacks and respond proactively to stop cyberthreats. - Security Command Center
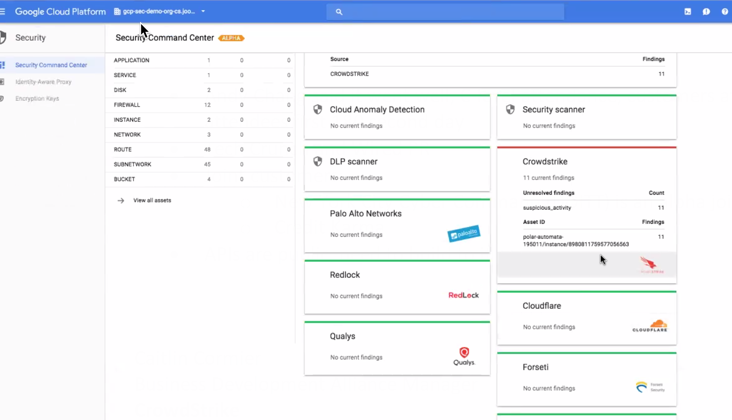
Automatically aggregate alerts from the Falcon platform in addition to other partner data sources to derive contextual insights. You can gain a comprehensive view of security and compliance across the GCP environment with a single unified management dashboard. - Google OS Configuration Management
With automated sensor deployment, you can easily install the lightweight Falcon sensor for new Compute Engine resources on Google Cloud. Maintain your strong security stance by using a centralized repository to store Falcon sensor packages to simplify and scale software distribution, installation, and management processes. - BeyondCorp Enterprise
Share signal information in your environments to enable policies and make access decisions with enriched posture intelligence. BeyondCorp Enterprise users can leverage the Falcon platform and Zero Trust Assessment for complete protection of business data and applications through verified access controls. Secure your assets and users from the sophisticated tactics of cyber adversaries including unwanted lateral movement.
Get Started
Defense in depth with cloud-scale cybersecurity strategies
- Google Chronicle
- Security Command Center
- Google OS Configuration Management
- BeyondCorp Enterprise
Not A CrowdStrike Customer?
Try CrowdStrikeDetails
Built by
Google CloudCategories
Cloud Security Security AnalyticsRequirements
Falcon Insight XDR Falcon Intelligence Falcon PreventSupport





