CrowdStrike 2026 Global Threat Report: The definitive threat intelligence report for the AI era Download report
×
![]()
×
![]()
×
![]()
×
![]()
- 01
- 02
- 03
- 04
- 05
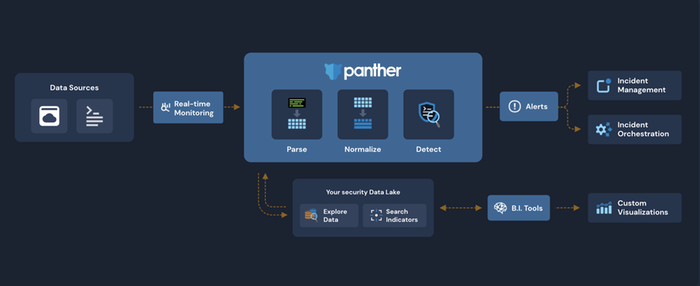
Your SIEM can't keep up. Run Panther with CrowdStrike Falcon®
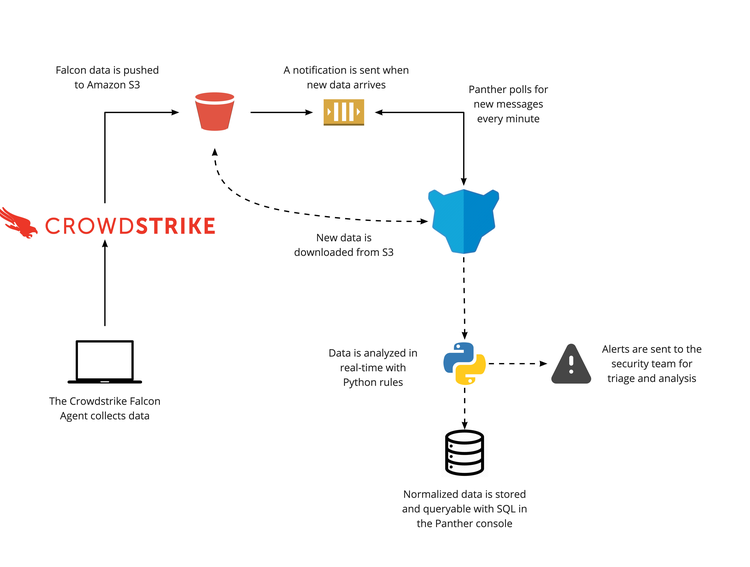
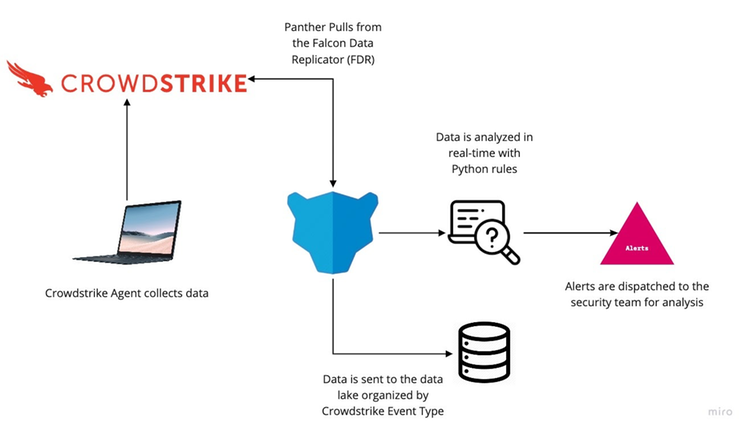
With Panther and CrowdStrike®, teams can write custom real-time detections, perform high-scale security analytics and correlation, as well as store Falcon telemetry for long-term storage. Monitor CrowdStrike logs to gain complete visibility into your network activity, DNS requests, and other security events with Panther‘s CrowdStrike integration. Panther can collect, normalize, and monitor CrowdStrike logs to help you identify suspicious activity in real-time. Your normalized data is then retained to power future security investigations.
- Correlate across structured security logs
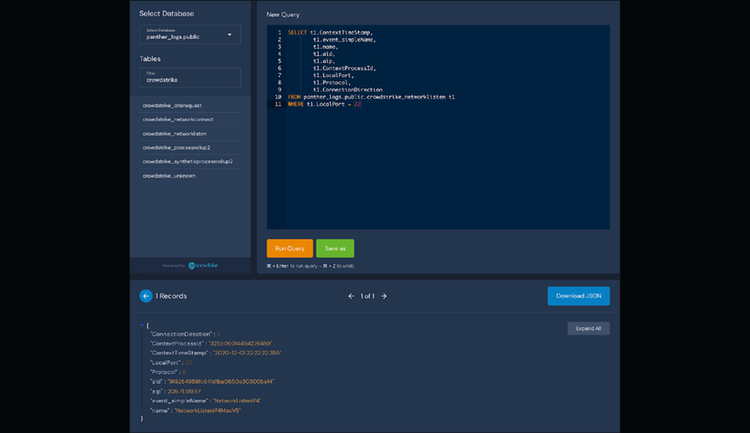
With Panther and CrowdStrike, teams can correlate activity across normalized CrowdStrike Falcon events with SQL to connect the dots during an incident. - High-scale investigations
Store Petabytes of Falcon Data Replicator (FDR) data in Panther's data lake for running investigations at a cloud-scale all with a high performance. - Real-time analysis
Receive notifications seconds after malicious activity occurs to decrease the blast radius of an attack. Panther utilizes Python-based detections for high expressibility.
Get Started
Empower security teams to detect breaches, anywhere
- Correlate across structured security logs
- High-scale investigations
- Real-time analysis
Not A CrowdStrike Customer?
Try CrowdStrikeDetails
Built by
PantherLabsCategories
IT and Security Operations Security AnalyticsRequirements
Falcon Insight XDRSupport




