CrowdStrike 2026 Global Threat Report: The definitive threat intelligence report for the AI era Download report
×
![]()
×
![]()
×
![]()
×
![]()
×
![]()
×
![]()
- 01
- 02
- 03
- 04
- 05
- 06
- 07
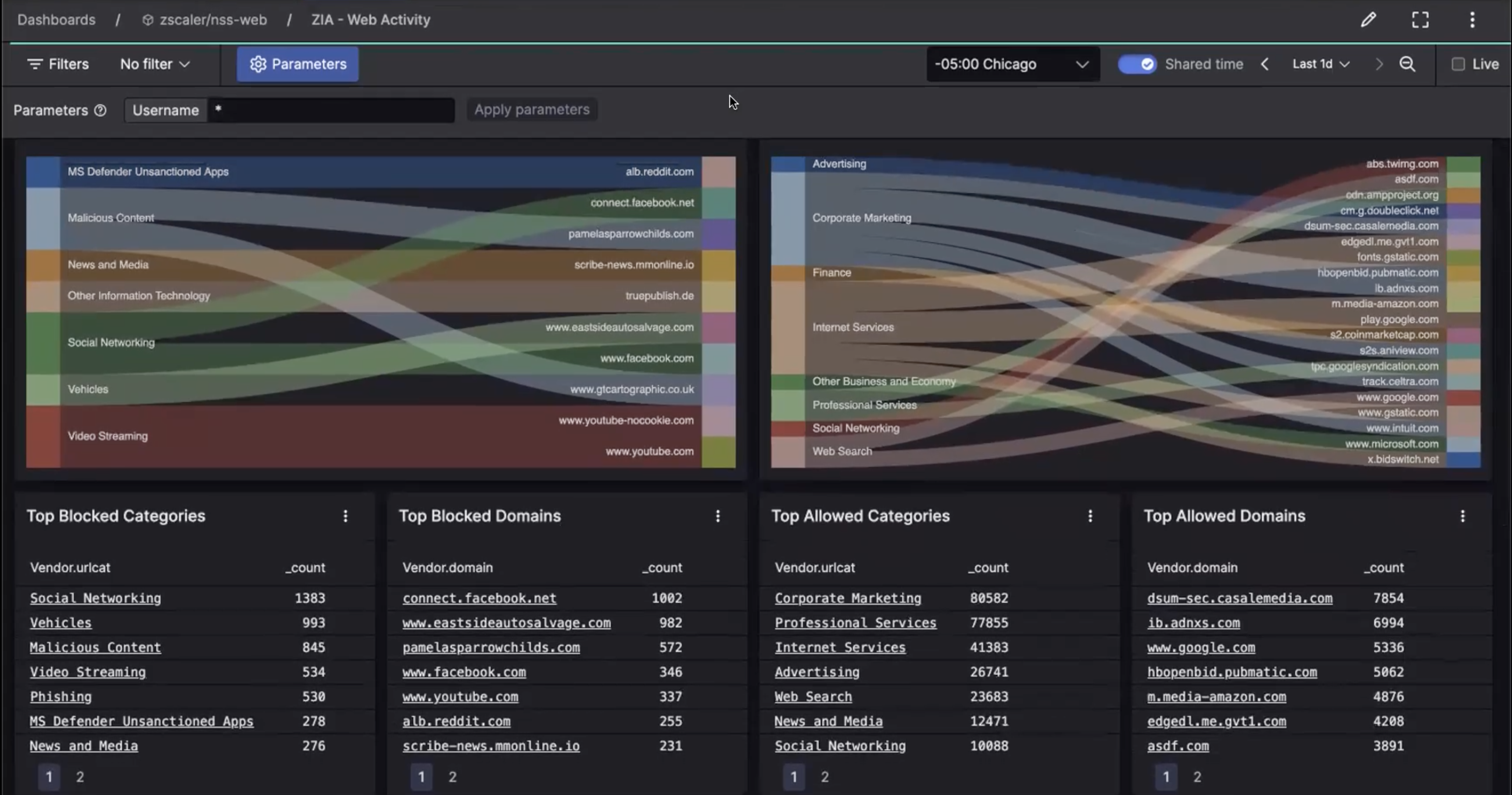
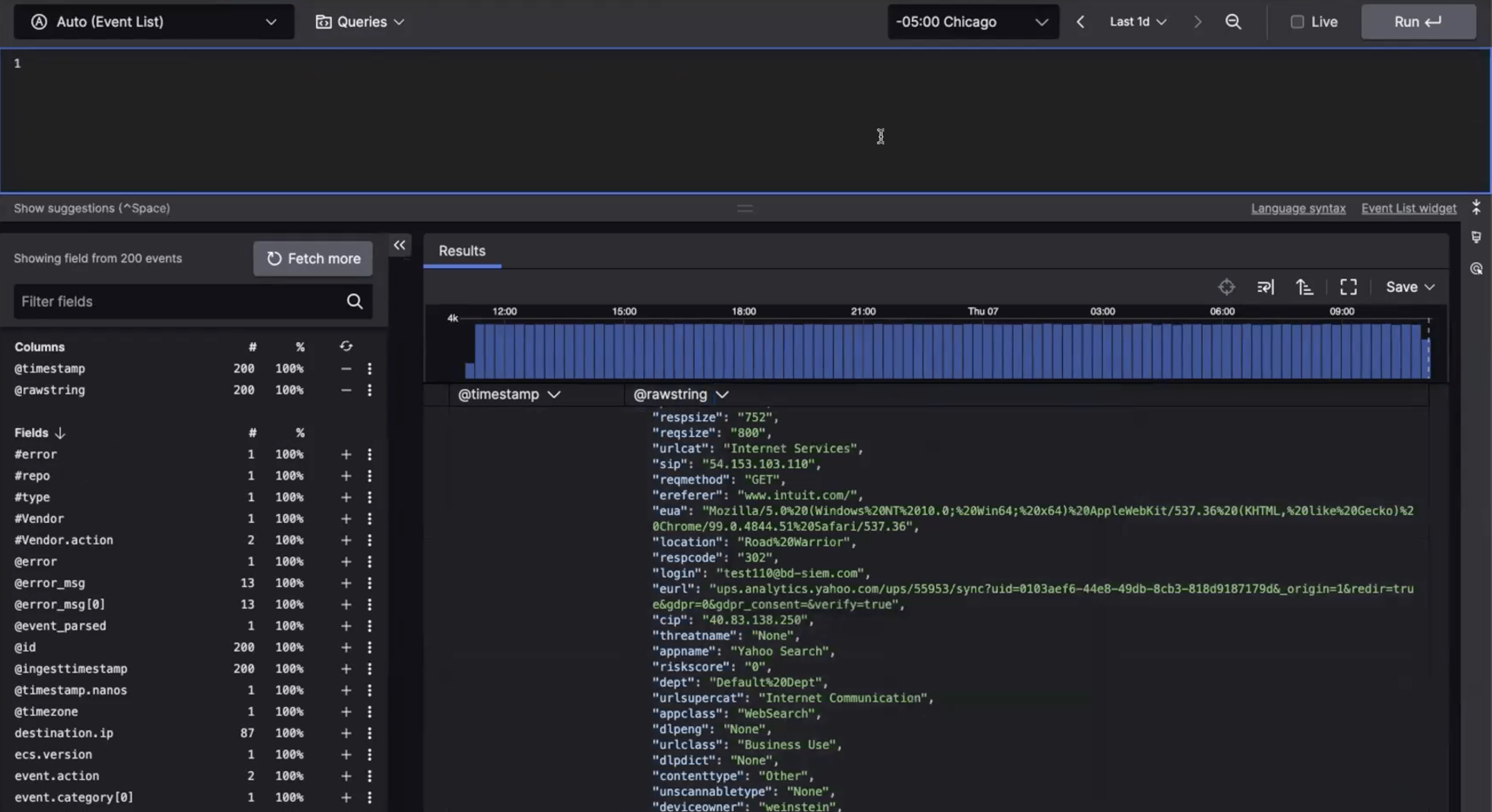
Enhanced insights with real-time logs for improved threat detection
Elevate threat detection and response using ZIA™ data in CrowdStrike Falcon LogScale. By real-time streaming of ZIA logs to Falcon LogScale, enjoy heightened Security Service Edge (SSE) visibility, alerting, cross-log correlation, and extended storage for more effective threat hunting, featuring tailored parsers and dashboards.
- Unify visibility in a single console
Effortlessly integrate and store ZIA logs in Falcon LogScale‘s central log management platform. This includes supporting default ZIA log formats in Falcon LogScale‘s HTTP Event Collector (HEC) for enhanced visibility and better threat detection and response - Visualize your data
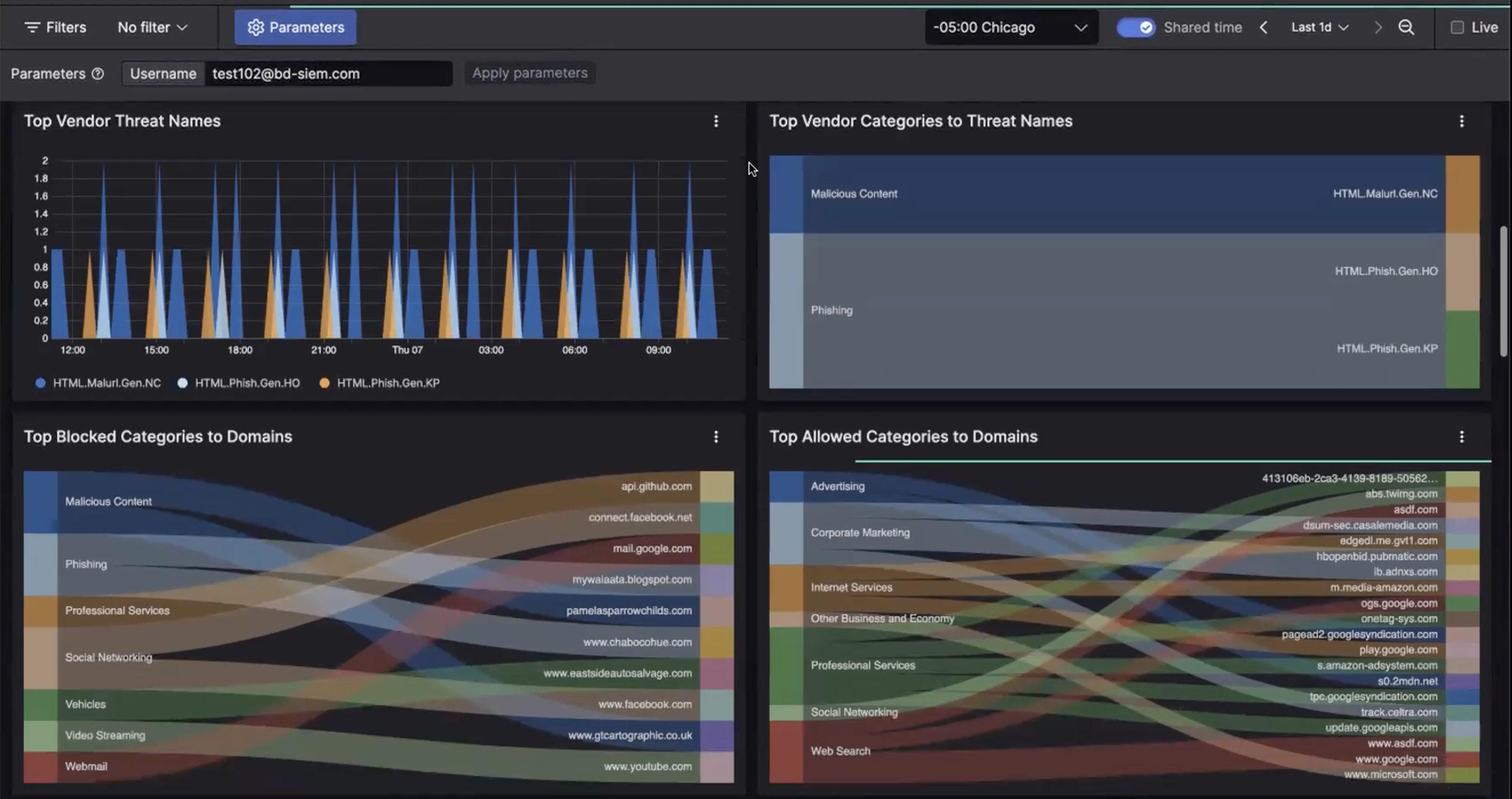
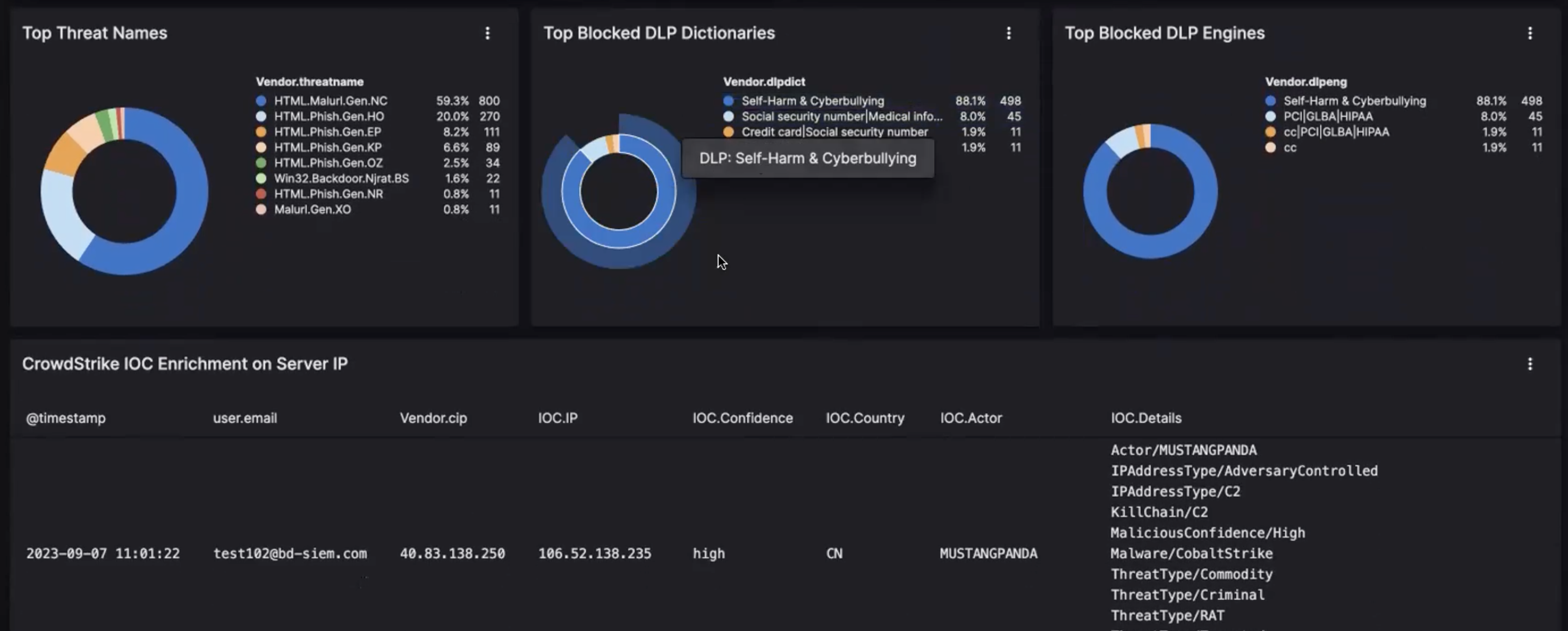
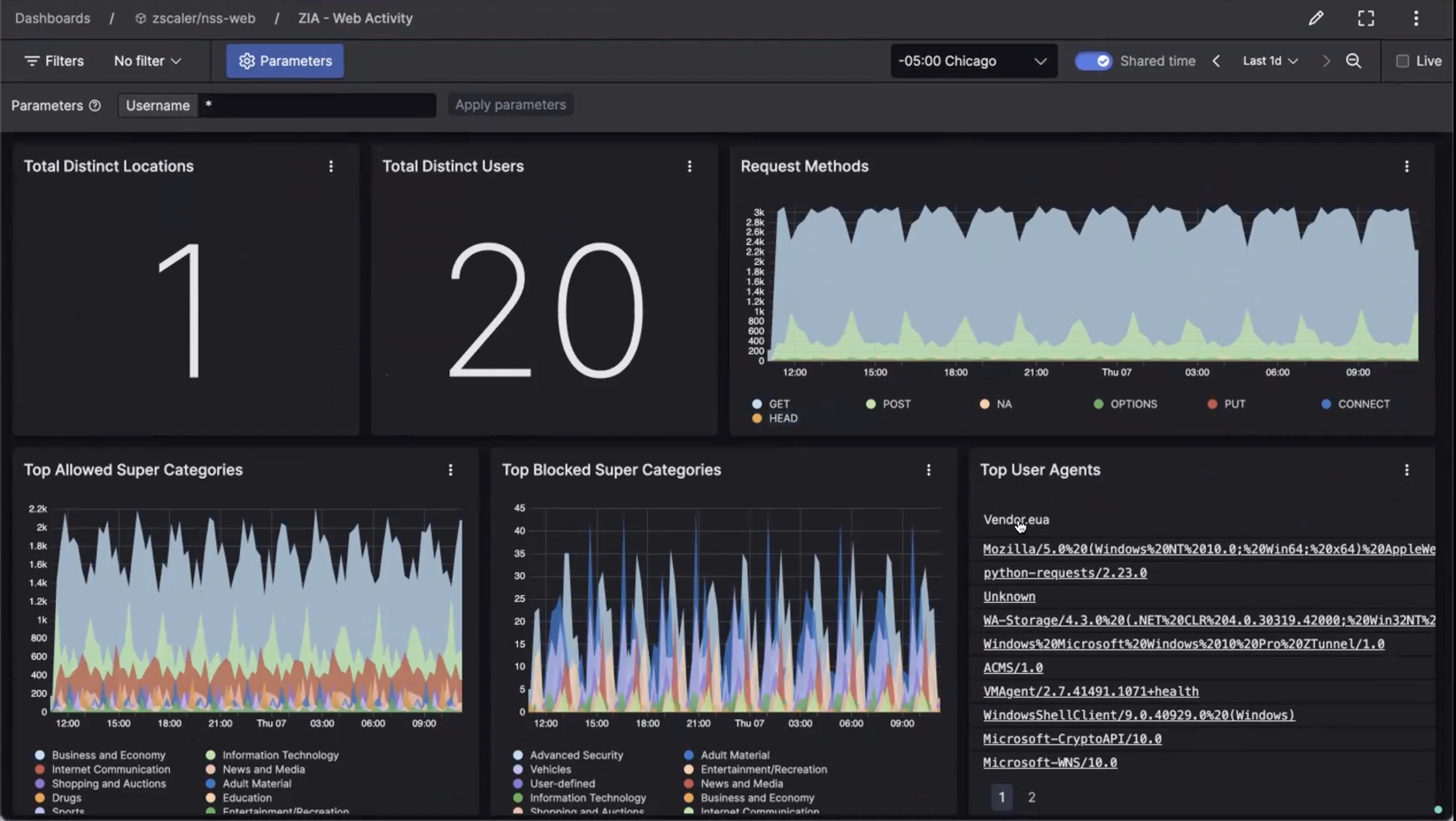
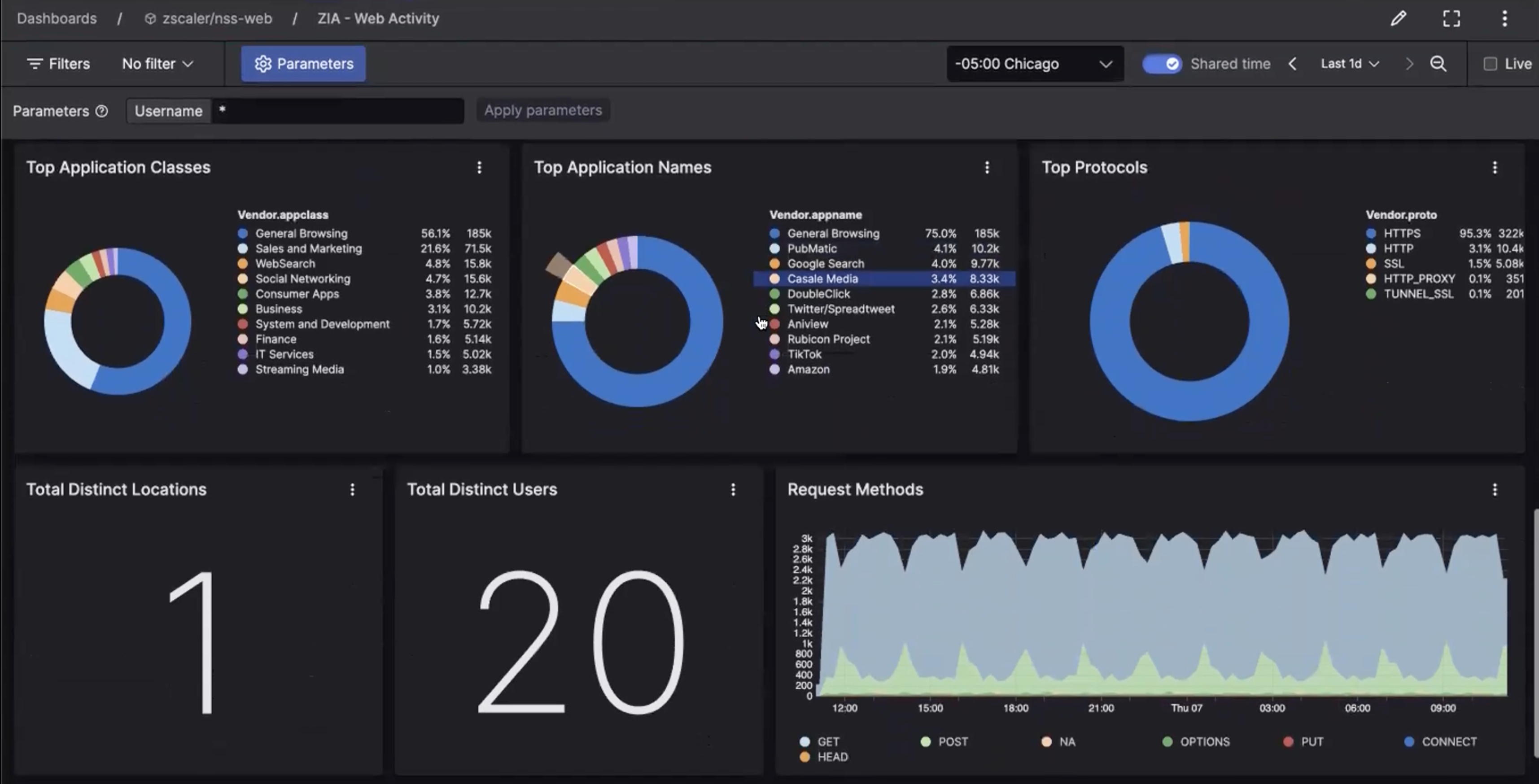
Efficiently monitor ZIA event logs through pre-built dashboards. These dashboards provide quick overviews of critical events across web traffic, web access control, firewall activities, and CASB functions
Get Started
Ingest and visualize ZIA logs in Falcon LogScale
- Unify visibility in a single console
- Visualize your data
Not A CrowdStrike Customer?
Try CrowdStrikeDetails
Built by
ZscalerCategories
IT and Security Operations Web SecurityRequirements
Falcon LogScale



